Is anonymity possible on the Internet? All this is the tip of the iceberg
Definition:
Anonymity is Namelessness, obscurity; silence, hiding the name.
Solution:
There should be nothing in the way between you and the Internet that can tie you to your connection. And you can't act as usual. In this case, your usual behavior at the same time should be recorded falsely.
You can find out who you are
1) Financial trail
purchasing devices and services that provided your access to the Internet
receiving benefits from the Internet in the form of finance, goods and services
2) Electronic trail
IP, MAC, time, built-in cameras, wifi, gsm, gps, microphone.
operating systems, programs, plugins, etc.
these little people scurrying around with mobile phones containing software for collecting information not only about the owner of the mobile phone but also about the surrounding radio air. GPS coordinates, base stations GSM, WiFi hotspots, bluethooth devices, etc. And there the blonde is talking on the phone, and her camera is quietly filming that you looked in her direction. This is not because it is a spy, but because it puts everything on the phone indiscriminately.
3) Metadata trail
handwriting: speed, characteristics Your work on the Internet. The typing style on the keyboard has its own imprint. Spelling errors, correctable typos, punctuation, etc. The Google search string in any browser using JS (if allowed) is transmitted to the Google server continuously while you are typing. Consider that information about the nature of the set is transmitted to the Internet. Google does everything to know your face even if it is wearing a mask. Don't forget about the mouse or touchpad.
the information you are looking for without an anonymous mask can give you away if you try to do the same in a mask. You need to have clearly written instructions on what not to do and clearly limited actions. Your anonymous life should be similar to the everyday life of a spy. This is self-discipline, this is work, this is a constant replenishment of knowledge and its application in practice. It is very difficult not to get burned in practice when they are watching you for 24 hours and do it without straining.
With regret, let’s keep silent about the fact that your friends will carefully write your name, date of birth, relationship, photo next to your Nickname or phone number and upload it to Apple or Google, and all applications that have access to the address book (and only the lazy don’t go there) know this immediately .
You can steal an Internet connection, buy a SIM card with GPRS from gypsies, but how can you hide from the video cameras carefully placed all over the world? RFID chips from banks, libraries, and the metro are carefully placed in your pockets. The ID card becomes biometric and its presence in the pocket is public place imposed by law.
The more modern the computer and phone, the more likely it is to have a factory backdoor at the chip level, or a backdoor from a reseller or delivery service. You think that by installing Tails or Kali Linux you have solved the problem - you are mistaken, you also need to assemble a computer using lamps :). Or you carry your phone with you; it gives the provider information about where you were 24 hours a day. Gives him your daily habits. Here Vasya is going to work, here he is coming back from work. But suddenly Vasya disappeared from the radar, although usually at this time he travels along route A or B. Strange. Anomaly. And now if all this information falls into one hand and is analyzed, what happens? It turns out that the circle of suspects is sharply narrowing. Vasya is found on cameras in Mitino, buying a SIM card from a gypsy, or standing near the library in a car with a laptop on his lap.
And the fact that Vasya uses TOR, VPN and an unusual operating system is no secret to the provider. He just doesn’t care about Vasya for the time being. Recorded traffic can be opened later.
So I'll sign the words Artem
If you want anonymity on the Internet, do not use the Internet.
From month to month, topics pop up on underground forums - how to create maximum anonymity for yourself and become invulnerable, will VPN and pulled socks be enough, etc. heresy, which has become boring and which is already answered with memorized phrases like - They will find it if they want, there is no such thing as 100%.
We take shovels and stretchers.
No matter how sad it is to say this, we will still need a VPN, you can buy it, steal it, give birth to it, in short, how to get it is up to you. I wouldn’t bet on free ones, if you really don’t have any money, buy from kebrum, there are only 5-6 bucks per month tariffs, there are no restrictions, and there is a demo mode, if you don’t download torrents you can work in demo mode, it’s a no-brainer . Okay, somehow you got hold of the VPN, what next?
And then YES-YES-YES, that same TOR, download, install, everything works out of the box, although out of the box if you use Windows, you will have to fuck around a little under Linux, but your efforts will be rewarded, I personally built everything on Ubuntu 12, at first I spat, but now it’s just fucked up, I’ve got an erection. In general, the TOR that comes in the box has the same brake, so you need to configure it correctly, with this config, your TOR will fly faster than an airplane + countries that we don’t need will be excluded, that is, we will never get a Russian IP address as an option and we will constantly exit through American nodes, of course we will mow down under the Amer.
TOR Config
You can easily find out how and where to push it on Google.
ControlPort 9051 DirPort 9030 DirReqStatistics 0 ExitNodes (US) StrictExitNodes 1 ExcludeNodes (RU), (UA), (BY), (LV), (LD), (MT), (GE), (SU) ExitPolicy reject * : * Log notice stdout Nickname R1 ORPort 3055 RelayBandwidthBurst 10485760 RelayBandwidthRate 5242880 SocksListenAddress 127.0.0.1 StrictNodes 1 |
What we have is that we select Exit nodes only from the USA by explicitly specifying (US), all intermediate and input nodes will change by country except these: (RU),(UA),(BY),(LV),(LD),( MT),(GE),(SU), this list of countries was compiled by experienced carders, perhaps some other countries should be added to the list, if you know which ones, be sure to share. We don’t pay attention to all other values; if you want, you can read about each parameter separately on TOR’s offsite, provided that you know English language or using the translator from the giant.
This means that we have configured TOR, acquired a VPN, and the foundation is ready. As we know, all traffic on the Exit node in the tor is transparent and can easily be intercepted by an attacker, but we will not leave the bad guys a single chance. Let's build an SSH tunnel over this entire foundation. That is, this is what we get:
1.
We connect to the network via VPN, accordingly we become an American, the IP changes to American (you can build your own chains and, if you wish, configure them as you like, the countries can be any).
2.
Next, we launch our configured TOR; accordingly, TOR will work through the VPN channel we previously connected.
3.
We stretch an SSH tunnel proxied through the TOR network on top of everything available.
4.
At the output we have the IP address of the SSH tunnel. And encrypted traffic goes through the Exit node and not a single bad guy will decrypt it and burn your secrets.
5.
PROFIT!
We have already discussed the first two points, I think everyone understands everything. But let's take a closer look at stretching the tunnel. Since I have Ubuntu (for these things I recommend Linux, because the SSH tunnel under the windows is fucking unstable, you’ll spit), I’ll tell you how to do all this on Nix systems. In order to create an SSH tunnel, we need to have an SSH shell on some server, I won’t tell you how to do this, you can again - buy, steal, give birth. In short, roughly speaking, we bought an SSH shell on an American server, what next, and then we need to build another wall. In the console we write the command:
sudo proxychains ssh –D 127.0.0.1 : 8181 username @ 142.98.11.21 |
The proxychains command means that we launch ssh through our local TOR server on port 9050 (roughly speaking, we proxy our tunnel), then comes the –D parameter, which creates a socket on port 8181, and then the address itself SSH servers, where first comes the login, and then through the dog the server’s IP address. We press enter and see this bullshit:
| S-chain | -< > - 127.0.0.1 : 9050 - & lt ; > < > - 142.98.11.21 - & lt ; > < > - OK |
If you see OK, then screw it, we connected to the server via the TOR network, then enter the password, press enter again and minimize the console, meanwhile on the local host 127.0.0.1 on port 8181 we have a socket hanging, through which we will now access Internet.
There are so many letters, I hope everyone understands everything, although this is a confusing topic, but there is no other way to do it this operation will not work. Over time, get used to it and in a minute, you’ll be creating incredibly cool channels for yourself.
How will we be caught?
Let’s say you stole a million money and they announced a reward for your ass. Accordingly, I start looking for you. Let's look at how the chain will unwind.
1.
Since the final IP address of the SSH shell, don’t feed it bread, all efforts will be thrown there.
2.
Since our SSH shell goes through the TOR network, the chain changes accordingly every 10 minutes, Exit nodes, middle servers and incoming nodes change. It’s a hell of a mess here, I personally can’t even imagine how it will be possible to find anything in all this fucking. Our traffic is encrypted on all nodes, sniffing an Exit node will also not work, TOR chains can even be built across the whole world. So this is some kind of unreal, even if they find an Exit node, then they will have to look for a middle server. And all this requires funds, connections and a lot of other things, not every office will do this, it’s easier to forget.
3.
Let's assume that a miracle happened, the TOR network let us down and told us our IP address to the VPN. Well, what can I say - it all depends on the VPN server, administration, weather conditions and many more factors. It depends on your luck, either the VPN will hand over all your logs or not.
4.
Even if they determined your real IP address, they found out your country and city. This doesn't mean anything yet. Nobody canceled the left sim cards, the neighbor's Wi-Fi. Well, this is completely for paranoids like Bin Laden, according to some sources, his security was built exactly in the way that I am describing to you, although this is again a dead telephone. If you want to do it well, do it yourself! You can reinforce your invulnerability with the thought that if they want to find you, then they will need very good finances, because just imagine what an operative will have to do, at least to get logs from an SSH server, not to mention the TOR network.
5.
IN in this example I’m not considering the i2p network, this is shit about nothing at all, firstly, you will never get real speed from it, secondly, you won’t be able to log in to any site, because i2p is not friendly with cookies at all, thirdly, the output will be permanently German IP address. These are the main points that make you want to send i2p to a big juicy dick.
Safe surfing or digging in
You and I have successfully built 50 percent of our fortress, but it’s better to spend one day on all this, but then in a few minutes bring the system into complete deflation. But what is this fortress to us if we inherit? Let's make it more difficult and set our browser to be completely fucked up. That is, we will not allow our browser to give us away completely. Of all the browsers available in the world, only Firefox can be successfully customized, and that is what we will choose. To do this, download the latest portable version, Google to help, unpack and launch.
This will allow us to disable all unnecessary crap that can burn us, like Java, Flash, etc. unknown shit. Next we install the following plugins:

You don’t need to install a screenshot, page hacker and hackbar, it’s not for everyone, everything else should be required. Then we set the checkboxes as in this screenshot, this will not allow us to burn on cookies, that is, after closing the browser, all cookies will be deleted and will not appear in future problems if you accidentally forgot to build anonymous tunnels.

about< b > < / b >:config |
and look for the line geo.enable - set this value to false, this will allow us not to tie the browser to our location. So, we’ve sorted out the basic settings, now let’s configure the installed plugins.
NoScript
First of all, we set up NoScript, you don’t need any special intelligence there, just check the box – Deny all JavaScript and that’s it, although I still dug around and turned off all unnecessary notifications. Please note that when NoScript is enabled, some sites that contain Java scripts will not work for you; one way or another, sometimes you will still have to disable this plugin, because there is no way, or use mobile versions site. With the plugin disabled, we will burn a lot of data about ourselves, for example, browser version, screen resolution, color depth, language, operating system and much more, including your real IP address. So, it’s either all or nothing!

ModifyHeader
With this wonderful plugin, we will filter some of the transmitted headers, not all of them, of course, but only those that can be filtered, look at the picture and repeat after me.

Once finished, click on the face with the inscription Start, the plugin will be activated and will filter headings that we do not like. Let's move on.
FoxyProxy
This plugin allows us to easily switch between proxies, for example, you want to access the Internet bypassing the ssh tunnel, or vice versa, use the entire existing chain, or you only need TOR, there are many examples. Let's create the following diagram:

I have only 3 points here: work through TOR, work through a tunnel and direct traffic without any proxies.
Work via TOR is configured as follows: 127.0.0.1 port 9050 + you need to check the box in Socks5
Working through a tunnel, set 127.0.0.1 port 8181 (we specified this port when creating the ssh tunnel, you can choose any other), and also check the box for Socks5. We save and close everything.
In the first case, we will be able to access the Internet through a VPN, and then launch the browser through the TOR network; accordingly, our traffic will not be encrypted on the Exit node.
In the second case, all our traffic goes through a VPN, then we proxy the ssh tunnel through the TOR network, at the output we receive encrypted traffic and the IP address of the ssh server we have chosen.
In the third case, we completely disable all proxification and go online with the IP address of our VPN server.
This whole thing can be easily and conveniently switched with the mouse and you should not have any difficulties.

We are done manipulating with plugins, I hope I have conveyed to you the basics of all this junk, but if you don’t understand something, ask in the comments. Basically we made it for ourselves secure browser. Now we can surf the Internet and not be afraid that we can be identified by some signs, in fact, we disguised ourselves as an ordinary ordinary American, nothing gives us away. Here is the report itself, how we look to others:




Conclusions e
In this article, I introduced you to the possible concept of anonymity on the Internet. In my opinion, this is the optimal scheme, of course you can add DoubleVPN, Socks and three more boxes to this entire chain, but the speed will not be the same, it all depends on desire and degree of paranoia. I described all the pros and cons of the scheme above, I hope you liked it and it gave you some good thoughts.
Cookies and strategy
In addition to all this, I want to remind you that you should not forget about other precautions, for example, installing an English-language operating system, using virtual machines for menial tasks, changing macro addresses on network cards, encrypting hard disks, with each new connection, be sure to check your IP address on specialized resources, that is, connected a VPN - checked the IP address, connected TOR, checked again, and so on, as usual, there are situations when the VPN seems to have risen, but the IP has not changed, here and burned, so we definitely take into account all the little things, it’s better to check it a hundred times than to regret it for a hundred years later. Also, when making transactions, do not use ICQ, exclusively jabber and exclusively connect it through created tunnels; in extreme cases, you can get by with just TOR. Store all the money you earn online in LR or in YaD, then buy Bitcoin with it, and then all funds are withdrawn anonymously by anyone in a convenient way. After each transaction, change your Bitcoin wallet (it’s done in a couple of clicks), then pour all your funds into one that doesn’t appear anywhere. Don’t forget to proxy all the applications we work with, you can generally configure the entire system so that absolutely all programs will access the Internet through your tunnels, again, I’ll direct you to Google, there’s plenty of information about this. If Windows is overly important to you and you can’t or can’t stand Nix similar systems, then the same can be done under the windows, but believe me that there will be more hemorrhoids and stability will drop significantly, so be patient and study Linux if you have already chosen the dark side. With this I hasten to say goodbye to you! If anything is not clear, ask, I’ll clear it up! Bye bye!
All the information I have provided in this topic is given for informational purposes only and is not a call to action, all responsibility lies on your shoulders.
Upd:
Another one has been discovered in Firefox interesting thing, I'm telling you!
Enter in address bar browser: about:config
We are looking for the parameter: network.proxy.socks_remote_dns
We post it in: true
The browser is now configured to use the DNS servers of the SSH tunnel itself. For example, if you go to whoer.net with similar settings browser, you will see the DNS server of the country of the SSH tunnel, and not the DNS of your ISP or the OpenVPN server through which you access the Internet.
Last updated by at July 2, 2015.
It happens in life that you need 100% anonymity when using the Internet through a browser (I’ll do without examples, otherwise tough guys will come to the comments again and accuse me of incitement and threaten me with department “K”). How to make sure that sites on the Internet (for example Google) cannot identify you and record information about any actions in your file?
It happens that you turn on a VPN with “incognito” mode, you don’t log in anywhere, and AdSense suddenly scares you with painfully familiar ads. How does he determine who is who?
To answer this question, let's conduct an experiment. Let's open tabs in four browsers:
- Tor Browser 6.0.2 (based on Mozilla Firefox 45.2.0);
- Safari 9.0 (incognito mode);
- Google Chrome 52.0.2743.82 (incognito mode);
- Mozilla Firefox 46.0.01 (incognito mode).
And let's see what data they can collect about a person. What do we tell the site about ourselves by typing the URL in the address bar?
We provide unique image rendering options (Canvas Fingerprinting)


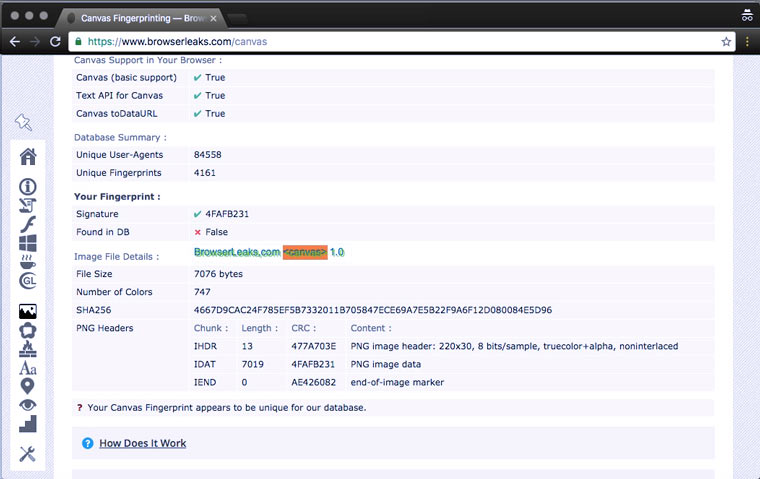
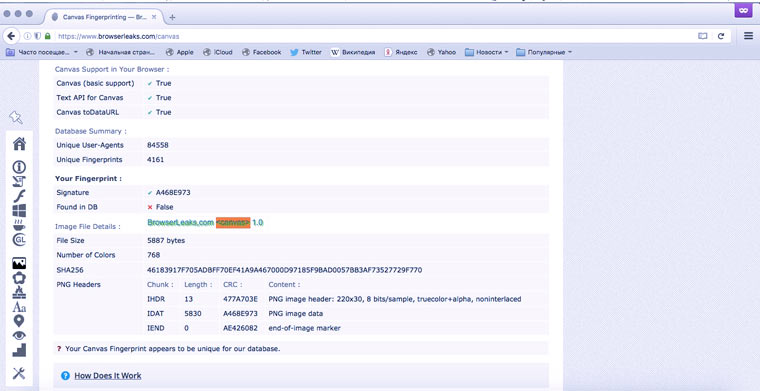
Canvas Fingerprinting is a user identification technology developed about 4 years ago at AddThis. The principle of its operation is based on the fact that when, when loading a page, a picture is drawn (rendered) (usually a single-color block in the background color with invisible text), the browser for this purpose collects a bunch of information about the system: what kind of hardware and graphics drivers, GPU version, OS settings, font information, anti-aliasing mechanisms and many other little things.
Together, this huge variety of details forms a unique characteristic that can distinguish a user's computer/browser combination from all others in the world. For each, it is written as a string similar to DA85E084. There are matches (according to Panopticlick, the average chance of finding a double is 1 in), but in this case, you can supplement them with other opportunities for identification (more on them below).
Tor asks permission to receive Canvas Fingerprinting, and if you are careful and do not give consent, you can keep this information to yourself. But all other browsers surrender their owner without a single peep.
You can read more about this identification method on Wikipedia.
We break through the database of advertising preferences




Many visited sites are now equipped with scripts for determining Canvas Fingerprint. Having received this unique value, one site can ask another for information about the person. For example, linked accounts, friends, IP addresses used and information about advertising preferences. Use the link below to check which systems have your consumer interests linked to Canvas Fingerprinting.
Tor again asked for the same permission as in the first point and, due to my refusal, nothing was found. Safari found me in 3 databases, Chrome in 13, and Firefox in 4. If you exit incognito mode, then in the latter the number of databases increases to 25, since most of them use good old cookies for identification.
We share the IP address and telecom operator




In Tor, you can change your “host country” using the New Identity button. And “incognito” modes do not hide your IP address (for this you must additionally use a proxy or VPN), but share your approximate location and information about your Internet provider with the site owners.
Revealing your city and the time in it (with geolocation services enabled)




On yandex.ru in Tor, without any location permissions, it showed where I was approximately and what time it was. It's the same with other browsers.
Send us your exact coordinates




Tor didn’t even ask permission to determine the coordinates and simply returned zeros. Safari, Chrome and Firefox asked standard definition(as in normal mode) and didn’t bother to remind me that I was encrypted and should not reveal such data.
Revealing your city and the time in it (with geolocation services disabled)




Then I turned off location services on the Mac and went back to yandex.ru. Tor made the site think that I was in Romania, but left the time in Moscow (due to the mismatch of IP and time zone, it will be possible to ban VPN providers at once in the event of a ban). In other browsers everything remains the same.


The fact is that Yandex does not need GPS (or WPS data from the device) to determine location. After all, he has a “Locator”! Logged into the network via Wi-Fi? The access point is already in the database (see article). Did you give yourself internet from your phone? The cell tower will be rented.
We provide information about language settings



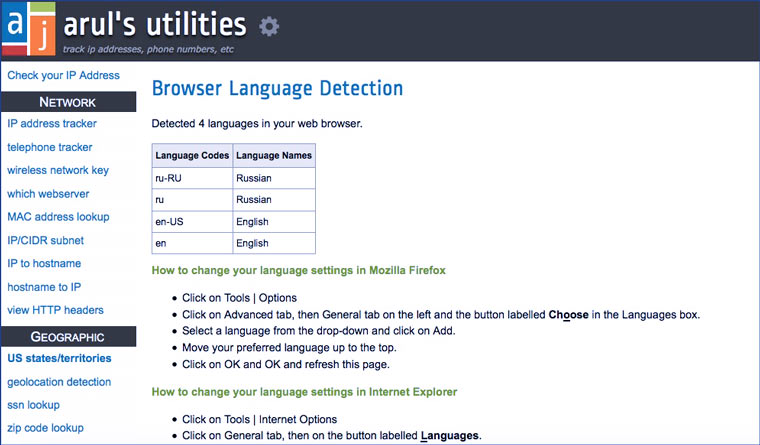
Another sure sign of a VPN lover is that the language does not match the country whose IP he is using. Tor let me down - its language is always English (but it can be changed, but I thought it should change automatically depending on the country). The rest of the settings are the same as in normal mode.
We tell you everything about your browser and system




Operating system, connection speed, monitor color characteristics, support different technologies, browser window width, Flash version- a bunch of little things that complement the unique characteristics of the user. Tor manipulates some of this data ( Windows example 7), and other browsers are absolutely honest.
A person can change the IP, turn on “incognito”, and the script to raise prices will quickly calculate: “Who is this guy who is coming to us with a slow Internet, old version flash and Windows XP for the second time, but now you decide to pretend to be a resident of Seychelles? We’re increasing it by 20%!”
We share a list of installed plugins




Another characteristic that adds uniqueness to a person is the list of plugins (with version information) installed in his browser. Tor hides them. Other browsers do not.
As you can see, Tor Browser provides good anonymity. But historical facts suggest that if a person does something really serious using the onion network, then he will still be sometimes they find. Everyone probably remembers the revealing story with the founder of Silk Road (a drug store) Ross Ulbricht.
And “incognito” modes are only needed to surf on someone else’s computer and not leave traces. In addition to them, you can block JavaScript, this will reduce the number possible ways identification, but many sites will become unusable.
Open the list of fonts installed on the system (=> programs)

In addition to the experiment, I would like to talk about another interesting function modern browsers. Any site can get a list of fonts installed on the system. Many applications have their own unique fonts and from them one can determine a person’s occupation. And based on this, show him advertisements. In Tor and incognito mode this does not work (or the list is too short).
All this is the tip of the iceberg
To protect against the above identification methods, there are special plugins for different browsers. But you shouldn't waste effort installing them. Since they cannot protect against the collection of all possible information.
After all, in the article I showed the simplest and clear examples how browsers collect information about us. But there could be much more of them: flash cookies, Silverlight cookies, time lag behind the standard time (many have at least 0.2-0.8 seconds) - many little things that would be superfluous. After all, the reader already understands that by opening a browser, he communicates himself to the world great amount information and demonstrates a set of unique characteristics that distinguishes his computer from all others.
What is the threat of all this information gathering?
You need to collect information about the majority of people on the planet for only one purpose - to increase the click-through rate of advertisements in order to earn more money from it. In principle, this is only beneficial - it is easier to find some goods or services.
More advanced identification methods are useful for stores to collect information about customers. So that a person cannot access the site under a different IP/disabling cookies and remain unrecognized. Language, time, rare font/plugin, monitor characteristics, typical error in search query the way you came - and that’s it! Take off your skates, we recognize you. There is no doubt, this is the same person who placed order #2389 a year ago. With this data, automated marketing systems can sell him more.
Or, naturally, all this can be used by the intelligence services. But who knows how everything works there.
So how can you be truly anonymous online?
No way. Use a new device purchased somewhere in the Caucasus to access the network, using Mobile Internet with a stolen SIM card, wearing a duck mask and leaving for the Kirov forests. Burn gadgets after use.
Yes, if you slightly modify Tor, then the problems described in the article can be protected. In addition, you can switch to Linux distributions Tails, Whonix or Tinhat, created for anonymous work. But how many unknown identification mechanisms are there? The same Canvas Fingerprinting hit the press in 2014, and began to be implemented in 2012.
Probably something is being developed/implemented now that is difficult to even imagine. Not to mention how to come up with a defense. Therefore, the question of anonymity on the Internet remains open.

27.01.2016 03.03.2016
What is the joy of the Internet?
In addition to the opportunity to make purchases in online stores, this is also an opportunity to anonymously insert your two cents on forums or leak streams of consciousness through personal blog. How was it before? A peasant came out to the square, shouted something wrong about the authorities, and they tied him up. In especially troubled times, there is no need to go anywhere - he inadvertently hinted at the work team and immediately some well-wisher will send a letter to the authorities about this.
Now - grace: say what you want, and no one will know. Because there is such a status - anonymous. Incognito, that is. He emerged from the sewer, farted loudly enough to make everyone howl, and dived back to the bottom. Nobody seems to know. This is where the great freedom of internet speech and other democracies come from.
Does anonymity really exist?
So? No not like this. Anonymity on the Internet is a ghostly and dubious thing. And they don’t catch those same anonymous people at their place of residence only for the reason that they are lazy and lack time. Millions of Elusive Joes leave millions of letters online every day and sweetly freeze at their own courage after each click of the “Send” button. And they don’t know that no one is interested in their messages, they do not pose a particular danger to the “elite”.
Tails- convenient, simple operating system, which does not require any special knowledge from the user. Used for anonymous web surfing, access to the “shadow” Internet and blocked sites, as well as for secure communication and file transfer over the network.
However, many of these millions in the last century would have been gladly attracted to socially useful work felling timber even for written letters. But the factor of too rapid development of technology is taking its toll. Technologies are developing faster than the bureaucratic and repressive apparatus. The Ministry of Internal Affairs and the KGB cannot adapt to working in conditions of complete internetization of the public in five years.
It can’t happen in five years, but in fifteen it’s easy. Today, individual units within the same Ministry of Internal Affairs and the KGB (no matter where they are called) are successfully searching the vast network for people who are truly worthy of their attention. They simply don’t care about ordinary people. But the personnel are trained, material base replenished, instructions are written. And the anonymous people who have briefly taken the lead will soon clearly see behind them the orderly rows of controllers and regulators catching up with them.
No privacy

Such data can be obtained by the administrator of any site.
And there is no more anonymity. Even the author of this blog, who does not consider himself an expert in computer security, can immediately name several ways to identify your computer on the network. In addition to the well-known IP address, it may even be a set of those installed in your Windows fonts. Together with the browser version, selected language, operating system version and other characteristics installed software, this information gives a completely unique “fingerprint” of your computer on the sites you visit. Let's add to this all sorts of browser and flash application cookies (which you cannot delete on your own). Let's remember about the gaining popularity wi-fi connections, constantly disseminating some information about themselves to all “grateful radio listeners” within a radius of several tens of meters. And so on and so forth.

Completely concealing one's true location and preventing identification of one's computer requires truly expert knowledge from the user. Which the vast majority, naturally, do not possess. Unlike those whose job is precisely to search for anonymous people of all kinds. So it turns out that there is not enough anonymity on the Internet today, and tomorrow there will be none at all. Moreover, it should be recognized that the work of competent authorities and simply curious individuals to identify the subject of interest to them has become much simpler today than 20 years ago! The saying “what is written with a pen cannot be cut down with an axe” is more relevant than ever! Everything that a stupid and impudent young man expresses on forums and social networks may subsequently poison his entire life, like an irreducible tattoo. Because Google (and all sorts of other search engines) now remembers everything.
Therefore, get used to taking what you do online seriously today. Or become a real computer security specialist.
It sometimes happens that fantasy and spy stories turn out to be not only the fruit of the author’s sick imagination, but the real truth. Just recently, some paranoid film about total state surveillance of a person was perceived as just another fairy tale, a play of the imagination of the author and screenwriters. Until Edward Snowden released information about PRISM, a user tracking program adopted by the US National Security Agency.
Cause for concern
After this news, jokes about paranoia became completely irrelevant. And talk about surveillance can no longer be attributed to a shattered psyche. A serious question arises: should you feel safe using your email or communicating on a social network or chat? After all, many large companies have agreed to cooperate with intelligence services: Microsoft (Hotmail), Google ( Google Mail), Yahoo!, Facebook, YouTube, Skype, AOL, Apple. Considering that PRISM was aimed primarily at surveillance of foreign citizens, and the volume of intercepted telephone conversations And emails according to some estimates, reached 1.7 billion per year, it is worth seriously thinking about how to protect your privacy from prying eyes.
Tor
The first reaction to the news about PRISM was the same for many: we won’t allow ourselves to be monitored, we’ll install Tor. This is, perhaps, in fact the most popular remedy, which we have talked about more than once on the pages of our magazine. It was also created by the American military, although for completely opposite purposes. Such is the irony. Users run Tor software on their machine, which works as a proxy; it “negotiates” with other network nodes and builds a chain through which encrypted traffic will be transmitted. After some time, the chain is rebuilt and other nodes are used in it. To hide information about the browser and installed OS from prying eyes, Tor is often used in conjunction with Privoxy, a non-caching proxy that modifies HTTP headers and web data, allowing you to maintain privacy and get rid of annoying advertising. To avoid climbing configuration files and don’t have to edit all the settings manually, there is a wonderful GUI shell - Vidalia, available for all OSes and allowing you to open the door to your PC in a couple of minutes anonymous world. Plus, the developers tried to simplify everything as much as possible, allowing users to install Tor, Vidalia and the portable version of Firefox with various security add-ons in one click. For secure communication, there is a decentralized anonymous messaging system - TorChat. To securely, anonymously and transparently redirect all TCP/IP and DNS traffic through the Tor anonymizer network, use the Tortilla utility. The program allows you to anonymously run any software on a Windows computer, even if it does not support SOCKS or HTTP proxies, which was previously almost impossible to do under Windows. In addition, for the standard Tor + Vidalia + Privoxy combination there is a worthy alternative - Advanced Onion Router bit.ly/ancXHz, a portable client for “onion routing”. For those who are especially concerned about their security, there is a Live CD distribution that is configured out of the box to send all traffic through Tor - bit.ly/e1siH6.
The main purpose of Tor is anonymous surfing plus the ability to create anonymous services. True, you have to pay for anonymity with speed.
I2P
In addition to “onion routing,” there is also “garlic” routing, used in I2P. Tor and I2P, although somewhat similar in appearance, largely implement diametrically opposed approaches. In Tor, a chain of nodes is created through which traffic is transmitted and received, while in I2P “incoming” and “outgoing” tunnels are used, and thus requests and responses go through different nodes. Every ten minutes these tunnels are rebuilt. “Garlic routing” implies that a message (“garlic”) can contain many “cloves” - fully formed messages with information on their delivery. One “garlic” at the moment of its formation can contain many “cloves”, some of them may be ours, and some may be in transit. Whether this or that “clove” in the “garlic” is our message, or whether it is someone else’s transit message that passes through us, only the one who created the “garlic” knows.
The main task of I2P, unlike Tor, is anonymous hosting of services, and not providing anonymous access to global network, that is, hosting websites on the network, which in I2P terminology are called eepsites.
For work software I2P requires pre-installed Java. All management is carried out through the web interface, which is available at 127.0.0.1:7657. After all the necessary manipulations, you need to wait a couple of minutes until the network is configured, and you can use all its hidden services. In this case, we received anonymous access to the I2P network, that is, to all resources in the .i2p domain. If you want to access the global network, then simply set the use of the proxy server 127.0.0.1:4444 in the browser settings. Exit from I2P to the global network is carried out through certain gateways (called outproxy). As you understand, you can’t count on great speed in this case. Plus, there is no guarantee that no one will sniff your traffic on such a gateway. Is it safe to post your anonymous resource on an I2P network? Well, no one can give a 100% guarantee of security here; if the resource is simply vulnerable, then it will not be difficult to determine its true location.

Obfsproxy
In many countries, such as China, Iran, providers are actively fighting against the use of Tor, using DPI (deep packet inspection), filtering by keywords, selective blocking and other methods. In order to bypass censorship, torproject released a special tool obfsproxy bit.ly/z4huoD, which converts traffic between the client and the bridge in such a way that it looks completely harmless to the provider.
GNUnet
What about secure and anonymous file sharing? For this purpose, you can resort to the help of GNUnet bit.ly/hMnQsu - a framework for organizing a secure P2P network that does not require centralized or any other “trusted” services. The main goal of the project is to create a reliable, decentralized and anonymous system exchange of information. All network nodes act as routers, encrypt connections with other nodes and maintain a constant level of load on the network. As with many other solutions, nodes that are actively participating in the network are served with higher priority. To identify objects and services, a URI is used that looks like gnunet://module/identifier, where module is the name of the network module, and identifier is a unique hash that identifies the object itself. An interesting feature is the ability to configure the level of anonymity: from zero (not anonymous) to infinity (the default is one). For secure transmission, all files are encrypted using ECRS (An Encoding for Censorship-Resistant Sharing). GNUnet is extensible and new P2P applications can be built on top of it. In addition to file sharing (most popular service), exist alternative services: a simple chat, currently in a half-dead state, as well as distributed DNS. Well, as usual, you have to pay for anonymity: high latency, low speed and fairly high resource consumption (which is typical for all decentralized networks). Plus there are problems backward compatibility between different versions framework.

RestroShare
RestroShare bit.ly/cndPfx is an open cross-platform program for building a decentralized network based on the F2F (Friend To Friend) principle using GPG. The core philosophy is to share files and communicate only with trusted friends and not the entire network, which is why it is often classified as darknet. To establish a connection with a friend, the user needs to generate a GPG key pair using RetroShare (or select an existing one). After authentication and asymmetric key exchange, an SSH connection is established using OpenSSL for encryption. Friends of friends can see each other (if users have enabled this feature), but cannot connect. This is how it turns out social network:). But you can rummage through folders between friends. There are several communication services online: private chat, mail, forums (both anonymous and with basic authentication), voice chat (VoIP plugin), channels like IRC.

Raspberry Pi
You might be wondering: what does Raspberry Pi have to do with it? We are talking about anonymity. And despite the fact that this small device will help achieve this anonymity. It can be used as a router/client, giving you access to Tor/I2P networks or anonymous VPN. Besides this, there is another plus. In decentralized networks, it is possible to achieve an acceptable speed of access to intranet resources only if you are constantly in it. For example, in I2P, the trust of other “garlic routers” in such a node will be greater, and accordingly the speed will be higher. It’s unreasonable to keep your computer constantly on for this purpose or to start a separate server, but it doesn’t seem like a shame to spend only $30 on it. You can use it in everyday life normal connection, and when you need to anonymously go online, you just let all the traffic go through the mini-device and don’t worry about any settings. It must be said that until recently there was no point in installing I2P software written in Java on Blackberry. The resource-hungry Java machine did not have enough of the standard 256 MB of RAM. With the release of the Raspberry Pi model B, which already carries 512 MB on board, this has become quite possible. So let's look at the main points related to installation. Let's say we are using Raspbian. First of all, let's update:
Sudo apt-get update; sudo apt-get dist-upgrade
Then we install Java, but not the standard one from the packages, but special version, sharpened under ARM processors, -bit.ly/13Kh9TN (as practice shows, the standard one will eat up all the memory). Download and install:
Sudo tar zxvf jdk-8-ea-b97-linux-arm-vfp-hflt-03_jul_2013.tar.gz -C /usr/local/java export PATH=$PATH:/usr/local/java/bin
Then download and install I2P:
Cd ~ mkdir i2pbin cd i2pbin wget http://mirror.i2p2.de/i2pinstall_0.9.7.jar java -jar i2pinstall_0.9.7.jar -console
To turn Raspberry into an I2P router, you need to do a little magic with the configs. Go to ~/.i2p and start editing the clients.config file. There we need to comment out the line
ClientApp.0.args=7657::1,127.0.0.1 ./webapps/
and uncomment
ClientApp.0.args=7657 0.0.0.0 ./webapps/
And then in the i2ptunnel.config file replace the addresses in the lines
Tunnel.0.interface=127.0.0.1 tunnel.6.interface=127.0.0.1
to 0.0.0.0 . Then we can start the I2P router by running:
Cd ~/i2pbin ./runplain.sh
Can also be added to crontab following lines so that the software is automatically raised when the system starts or after a crash:
0 * * * * /home/pi/i2pbin/runplain.sh @reboot /home/pi/i2pbin/runplain.sh
All that remains is to organize remote access to the device. The best way- use dynamic portforwarding via SSH. To do this, you just need to set up an I2P tunnel in the settings, which would point to the 22nd port on local machine. In the same way, you can turn the Pi into an anonymous VPN (how to do this, you can see here -http://bit.ly/11Rnx8V) or connect to Tor (an excellent video manual on this http://bit.ly/12RjOU9) . Or you can come up with your own way to use the device for anonymous travel on the Internet.
Mikrotik
In fact, the Raspberry Pi is not the only small device on the basis of which you can organize anonymous access to the Network. A worthy alternative he will have a router from the Latvian company MikroTik, which produces network equipment and software for it. Such a device will cost a little more, but will require less fuss when setting up. Among the company's products RouterOS is an operating system based on Linux based, designed for installation on MikroTik RouterBOARD hardware routers. Various options RouterBOARD platforms allow you to solve various network problems: from building a simple access point to powerful router. Despite the presence of a power connector, almost all devices can be powered using PoE. A big plus is the availability of good documentation http://bit.ly/jSN4FL, which describes in great detail how you can create a security router based on RouterBOARD4xx by connecting it to Tor networks. We will not dwell on this; everything is described in great detail.

VPN
When talking about privacy and anonymity on the Internet, we cannot ignore the use of a VPN for these purposes. We have already talked about how to set up your own VPN server in the Amazon cloud bit.ly/16E8nmJ, and we looked in detail at installing and fine-tuning OpenVPN. You can see all the necessary theory in these articles. However, I would like to remind you once again that VPN is not a panacea. Firstly, there may be situations where traffic can “leak” past the VPN connection, and secondly, in networks based on PPTP protocol, there is a real possibility of decrypting the intercepted data (“Such an insecure VPN,” ][Aker #170). So you should not believe in complete security when using virtual private networks.
Summing up
These are just the most popular solutions that allow you to somehow protect your privacy from the prying eyes of Big Brother. Perhaps in the near future new technologies will appear or we will all actively use one of the ones discussed today. Who knows... Whatever it is, it is important to always remember that no solution can ever provide a 100% guarantee of security. Therefore, do not feel completely safe by installing Tor, I2P or anything else - many have already paid for the feeling of false security.
