Data exchange protocols over serial communication lines SLIP and CSLIP.
Introduction
Actually SLIP And PPP are protocols that adapt IP for working on serial lines. They represent a kind of spacer between IP and modem protocols. SLIP And PPP It makes sense to use it in conjunction with high-speed modems on fairly high-speed lines.
Main function of the software SLIP/PPP- arrange shipment IP-packets over a serial line, which does not provide for dividing the transmitted information into any separate blocks and sends all data in a single continuous stream. SLIP/PPP is precisely engaged in organizing such a transfer so that at the other end this continuous and continuous data stream can be divided into its components IP-packets, select them and pass them on as IP-packages.
SLIP/PPP very convenient for connecting a home computer to a local network, which, in turn, is part of the Internet. For example, you can use PPP to connect your home personal computer to your organization's network. And then your computer will have the same Internet capabilities as any other computer in your organization connected to the Internet via Ethernet.
SLIP/PPP They are also suitable for connecting a home computer (or a very small local network) to the provider itself, which can provide direct access to the Internet.
However, it should be understood that these protocols are not generally intended for connecting medium-sized or large networks to the Internet: they are not designed to work on high-speed lines that are required to serve a large number of users.
SLIP and CSLIP protocols
The first de facto standard allowing devices connected by a serial communication line to operate using protocols TCP/IP, there was a protocol SLIP
(Serial Line IP), created in the early 80s and built into OS 4.2 Berkley UNIX in 1984 by Rick Adams. Later SLIP was supported in other versions of UNIX and implemented in PC software.
The popularity of the SLIP protocol is explained by the fact that it made it possible to connect to Internet networks through standard port RS232, available in most computers. Currently, SLIP is widely used mainly on home computers connected to serial lines, which have a throughput from 1200 bps to 19.2 Kbps.
Restrictions
Connection via SLIP (Serial Lines Internet Protocol). Each protocol has the property of encapsulating data. Protocol SLIP uses special characters to delimit a frame of data on a serial link. In order to recognize the boundaries of SLIP frames transmitted over a serial link and to separate one frame from another, the SLIP protocol uses special character END, whose hexadecimal value is C0. The use of a special character can create a conflict: if the byte of the transmitted data is identical to the END character, then it will be erroneously identified as a sign of the end of the frame. To prevent this situation, a data byte with a value equal to the value of the END character is replaced by a composite two-byte sequence consisting of the special character ESC (DB) and the DC code. (The ESC character used in the SLIP protocol is not equal to the ESC character in ASCII encoding, we will denote SLIP ESC.) If the data byte has the same code as the SLIP ESC symbol, then it is replaced by a two-byte sequence consisting of the SLIP ESC symbol itself and the DD code. After the last byte of the packet, the END character is transmitted.
The mechanism of formation of compound sequences is shown in Fig. 1. Here are a standard IP packet, one byte of which is identical to the END character, and the other to the SLIP ESC character, and the corresponding SLIP packet, which is 4 bytes larger.
Although the protocol specification SLIP not determined maximum length transmitted SLIP frame, its actual size is determined by the length IP packet and should not exceed 1006 bytes. This limitation associated with the first implementation of the protocol SLIP in the corresponding driver for Berkley Unix, and compliance with it is necessary to maintain compatibility between different implementations SLIP
.
Popularity of the protocol SLIP This is explained by the fact that it made it possible to connect to the Internet via the standard RS 232 port found on most computers. Control program SLIP loaded and unloaded as needed. Most management programs SLIP have the opportunity to recruit phone number provider.
Software that implements working with the protocol SLIP(TCP-manager), performs the functions of managing a network device, that is, it is the driver of a network device, such as a modem. It accepts IP-packets from the program (more precisely, the process) sending them (from the program network layer), covers it with its service information and transmits it to a serial data transmission device (modem, serial port, etc.). At the other end of the serial line, a similar program receives characters coming from a serial data transmission device, frees them from service information and transmits what was received and should be received at the same time IP-packets corresponding to the program (network layer) that processes IP-packages.
Restrictions. To establish communication using the SLIP protocol in the TCP/IP protocol stack, computers must have information about each other's IP addresses. However, it is possible that, say, when making a connection between a host and a router, the latter will need to transfer information about its IP address to the host. But the SLIP protocol does not have mechanisms that make it possible to exchange address information. This limitation prevents the use of SLIP for some types of network service. For example, every time after establishing SLIP-connection, the computer turns into a full-fledged Internet host with its own IP-address. If the provider uses dynamic assignment IP-addresses, then with each new connection the computer will receive a new IP address. Consequently, other computers on the network will be forced to look for it under an unknown address.
Another disadvantage of SLIP is the lack of indication of the type of protocol whose packet is encapsulated in the SLIP packet. Therefore, only one traffic can be transmitted via a serial line using the SLIP protocol. network protocol.
When working with real telephone lines, noisy and therefore distorting the transmitted data, error detection and correction procedures are required. The SLIP protocol does not provide for such procedures. These features provide:
- Or higher-lying protocols, for example, in the TCP/IP stack, the IP protocol tests the integrity of the packet using the IP header, and one of the two transport protocols (UDP or TCP) checks the integrity of all data using checksums. However, in the protocol UDP it is not necessary to use checksums, so sharing UDP And SLIP undesirable.
- Or underlying protocols. Since to establish a connection using the protocol SLIP Typically a modem is used that operates over a telephone line and is connected to an asynchronous serial port. Two computers that have established such a connection exchange data with pauses of variable length. Unfortunately, there is always interference in the telephone line, otherwise known as noise, so modems connected to telephone network, distinguish data from possible interference using various communication parameters. When using a modem and communication software, certain communication parameters are configured, such as speed, data size, parity check. For two modems to communicate successfully, both of them must be configured identically.
The absence of these features makes the protocol SLIP very easy to implement and therefore popular.
Compressed SLIP
Low throughput serial lines makes it necessary to reduce the transmission time of packets, reducing the amount of service information contained in them. This problem is solved using the protocol Compressed SLIP, which supports packet header compression. This protocol was created at Lawrence Berkeley Labs (LBL) by Van Jacobson as a way to improve the serial transmission efficiency and service level of application programs using TCP/IP on slow lines. Appearance CSLIP This is explained by the fact that when using programs like telnet, rlogin and others, to send one byte of data, you need to send a 20-byte packet header IP and a 20-byte packet header TCP. Specification CSLIP provides compression of 40 bytes of header to 3-5 bytes.
On low speeds data transfer, this difference is noticeable only when working with packets carrying small amounts of information; such packets are generated, for example, when working telnet or rlogin. At high speeds CSLIP gives a smaller gain and almost nothing for packets with large amounts of data, for example, ftp-packages.
CSLIP To forward the packet, it uses information from the previous packet, i.e. transmission has a chain structure. The first packet in the chain is uncompressed. If any packet is lost, then the chain is broken, the same packet cannot be requested at the very end, it must be sent again right there, i.e. stop the transfer process and start a new chain. Thus, this technology, with frequent packet loss or corruption, leads to greater time losses than conventional SLIP. This occurs due to delays in stopping and transmitting a new uncompressed packet.
PPP (Point-to-Point Protocol).
Bibliographic information
At the end of the 1980s. The Internet (a large international network connecting many research organizations, universities and commercial concerns) began to experience a sharp increase in the number of mainframe computers providing TCP/IP. The vast majority of these main computers were connected to local area networks (LANs). various types, with Ethernet being the most popular. Most of the other main computers were connected through global networks(WAN) such as public networks data transfer (PDN) type X.25. A relatively small number of main computers were connected to point-to-point (point-to-point) communications links (ie, serial links). However, point-to-point communication channels are among the oldest methods of transmitting information, and almost every major Calculating machine supports direct connections. For example, asynchronous RS-232-C interfaces are found virtually everywhere.One of the reasons for the small number of communication channels IP with direct connection there was a lack standard protocol formation of an Internet data packet. Protocol Point-to-Point Protocol (PPP) (Direct Link Protocol) was intended to solve this problem. In addition to solving the problem of forming standard Internet data packets IP in channels with direct connection, RRR also had to solve other problems, including address assignment and management IP, asynchronous (start/stop) and synchronous bit-based packet generation, network protocol multiplexing, link configuration, link quality testing, error detection and variant negotiation for capabilities such as network layer address negotiation and information compression negotiation. RRR addresses these issues by providing an extensible Channel Control Protocol and families of Network Management Protocols Network Control Protocols (NCP) , which allow you to negotiate optional configuration parameters and various capabilities. Today PPP, besides IP, also provides other protocols, including IPX And DECnet .
Unlike SLIP- protocol RRR can operate over any DTE/DCE interface (for example, EIA RS-232-C, EIA RS-422, EIA RS-423 and CCITT V.35). Protocol PPP It is quite unpretentious and can work without modem control signals (such as Request to Send, Clear to Send, Data Carrier Detect and Data Terminal Ready). The only absolute requirement that makes RRR, is the requirement to provide redundant circuits (either dedicated or switchable) that can operate in either synchronous or asynchronous bit-sequential mode, transparent to data blocks link layer RRR . RRR does not impose any restrictions regarding the speed of information transfer, other than those determined by the specific DTE/DCE interface applied.
PPP Components
RRR provides a method for transmitting datagrams over direct-connect serial communication channels. It contains three main components:
Work algorithm.
In order to organize communication through a direct connection communication channel, initiating RRR first sends packets to select the configuration and (optionally) test the data link. After the channel is established and the necessary negotiation of optional means is carried out by the package, initiating RRR sends packets NCP to select and configure one or more network layer protocols. Once the configuration of each selected protocol is determined, datagrams from each network layer protocol can be sent via this channel. The channel retains its configuration for communication as long as explicit packets or NCP will not close this channel, or until some external event occurs (for example, the inactivity timer expires or some user intervenes).
can accommodate modifications to the standard data block structure RRR. However, modified data blocks will always be clearly distinguishable from standard data blocks. (See below for more details).
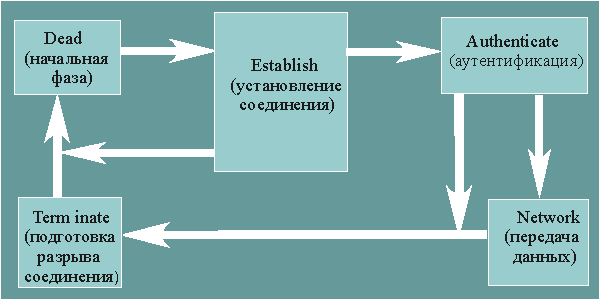
The Dead phase begins and ends the communication process. In the event of an external event (for example, readiness hardware communicate), the Establish phase will be initiated, in which various connection parameters are negotiated (packet exchange). If it is impossible to agree on a certain parameter, the process will be interrupted and the protocol will go into the Dead state. If all the necessary parameters are agreed upon, the Authenticate phase will be initiated, in which the authenticity of the session participants is checked (if any is required). If authentication fails, the Terminate phase will be initiated, preparing to terminate the connection. If the Authenticate phase is successful, the protocol moves to the Network phase. In this phase, data is sent in accordance with previously configured communication parameters (in particular, the type of network protocol). The Network phase begins with each network layer protocol (such as IP or IPX) configuring various parameters(say, negotiates a packet header compression algorithm, exchanges address information) using the appropriate Network Control Protocol (for example, IP Control Protocol or IPX Control Protocol). The Terminate phase (used when frames have finished transmitting or if any errors occur) terminates frame transmission and transfers the protocol RRR into Dead state.
PPP protocol frame structure.
RRR uses principles, terminology and procedure data block structure HDLC ( High Level Data Link Control) (ISO 3309-1979) of the International Organization for Standardization (ISO), modified by ISO 3309-1984/PDAD1. ISO 3309-1979 defines the data block structure HLDC for use in synchronous environments. ISO 3309-1984/PDAD1 defines proposed modifications to the ISO 3309-1979 standard that allow its use in asynchronous environments. Management procedures RRR use definitions and coding of control fields standardized by ISO 4335-1979 and ISO 4335-1979/Addendum 1-1979.
| 1 byte | 1 byte | 1 byte | 2 bytes | (up to 1500 bytes) | 2 bytes | 1 byte |
| Flag | Address | Control | Protocol | Information | CRC | Flag |
| (7E) | (FF) | (03) | (7E) |
Flag The length of the "flag" sequence is one byte; it indicates the beginning or end of a block of data. This sequence consists of the binary sequence 01111110. Address
The length of the "address" field is 1 byte; it contains the binary sequence 11111111, which is a standard broadcast address. RRR does not assign individual addresses to stations, that is, the contents of the "address" field never change.
Control The "control" field is 1 byte and contains the binary sequence 00000011, which requires the user to transmit information in a non-sequential frame. Connectionless services similar to those provided LLC Type 1. Protocol The length of the "protocol" field is 2 bytes; its value identifies the protocol contained in the information field of the data block. Field values Protocol and their corresponding packages
| Protocol field value | Package type |
| 0021 | IP |
| 0023 | ISO CLNP |
| 0025 | Xerox NS IDP |
| 0027 | DECnet Phase IV |
| 0029 | Apple Talk |
| 002B | IPX |
| 002D | Van Jacobson Compressed TCP/IP 1 |
| 002F | Van Jacobson Compressed TCP/IP 2 |
| 8021 | IP Control Protocol |
| 8023 | ISO CLNP Control Protocol |
| 8025 | Xerox NS IDP Control Protocol |
| 8027 | DECnet Phase IV Control Protocol |
| 8029 | Apple Talk Control Protocol |
| 802B | IPX Control Protocol |
| C021 | Link Control Protocol |
| C023 | User/Password Authentication Protocol |
Information The length of the “data” field is zero or more; it contains a datagram for the protocol specified in the protocol field. The maximum default length of an information field is 1500 bytes. According to a priori agreement, allowing implementations RRR may use other values for the maximum information field length.
If, during a synchronous type of communication, a byte with the value 7E (flag byte value) appears in the “data” field, then the situation is processed at the hardware level using the bit stuffing technique.
With an asynchronous (start-stop) type of communication, the situation is when bytes with values 7E or 7D (the value of the Esc - escape symbol) and values less than 20 (control ASCII characters), are processed using compound sequences. Byte 7E is transmitted as a two-byte sequence 7D,5E; byte 7D - as a sequence 7D,5D; XX bytes with values less than 20 - as XX, 01. CRC The Data Block Check Sequence (CSC) field is typically 16 bits (two bytes). According to a priori agreement, allowing implementations RRR may use a 32-bit (four-byte) CSC field to improve error detection.
Advantages.
Compared to the protocol SLIP protocol PPP is a much more advanced tool for working on serial lines and has the following advantages:
- possibility of simultaneous operation on various network protocols, and not only on IP ;
- checking data integrity by calculating the checksum;
- support for dynamic address exchange IP ;
- ability to compress headers IP- And TCP-packages developed by Van Jacobson (the mechanism is similar to that implemented in the protocol CSLIP).
Tests recently conducted by Morning Star Technologies showed that there was no significant difference in protocol performance SLIP And RRR No. The difference in the transmit-receive characteristics of computers and modems and even the quality of protocol implementation affects performance much more than the actual differences between the protocols.
Until recently, users of the protocol SLIP there were more than protocol users RRR, but this was mainly due to the small number of software products supporting RRR. However, there is now no doubt that the future lies with the protocol RRR. This is confirmed by the massive emergence of products that implement this protocol.
Among latest news- specification implementation Point-to-PointTunneling Protocol(US Robotic company together with Microsoft).
Link Control Protocol PPP (LCP)
LCP provides a method for establishing, configuring, maintaining, and terminating a directly connected channel. Process LCP goes through 4 clearly distinguishable phases:- Organization of the channel and coordination of its configuration. Before any network layer datagrams can be exchanged (e.g. IP), LCP must first open communication and agree on configuration parameters. This phase ends after the configuration confirmation packet has been sent and received.
- Determining the quality of the communication channel. LCP provides an optional link quality determination phase that follows the link establishment and configuration negotiation phase. This phase examines the link to determine whether the link quality is sufficient to call network layer protocols. This phase is completely optional. LCP may delay the transmission of network layer protocol information until this phase is completed.
- Coordination of network layer protocol configurations. After LCP will complete the link quality determination phase, the configuration of network protocols can be individually selected by the corresponding NCP, and they can be called and released at any time for later use. If LCP closes a given channel, it informs the network layer protocols so that they can take appropriate action.
- Termination of the channel. LCP can close the channel at any time. This is usually done at the request of the user (human), but can also occur due to some physical event, such as media loss or a timer expiring.
- Packages for organizing a communication channel. Used to organize and select channel configuration.
- Packets for channel termination. Used to terminate the communication channel.
- Packages to maintain the functionality of the channel. Used to maintain and debug the channel.
HDLC protocol
HDLC- high-level data link control protocol is published ISO standard and base for building other link layer protocols ( SDLC, LAP, LAPB, LAPD, LAPX And LLC). It implements a flow control mechanism through continuous ARQ(sliding window) and has optional capabilities (options) supporting half-duplex and full-duplex transmission, single-point and multipoint configurations, as well as switched and non-switched channels.
Flow control V HDLC carried out using transmitting and receiving windows. A window is installed at each end of the communication channel to ensure resource reservation for both stations. These resources can be compute resources or buffer space. In most cases, the window provides both buffer space and numbering rules (messages).
The window is set during the initiation of a communication session between stations. If station A and station B must exchange data, A reserves a window for B, and B reserves a window for A. The use of windows is necessary for full-duplex protocols because they involve a continuous flow of frames to the receiving node without periodic stop-and-wait acknowledgments.
Protocol SLIP (Serial Line IP, RFC-1055) is the simplest way to encapsulate IP datagrams for serial communications.
This protocol has become popular due to the ability to connect home personal computers to the Internet via the R.S.-232, which is connected to the modem. IP-datagram in case SLIP must end with a special character 0xC0 called end. In many implementations, the datagram begins with this character. If any byte of the datagram is equal to the end character, then the two-byte sequence 0xDB, 0xDC is transmitted instead. Octet 0xDB performs in SLIP function ESC-symbol. If the datagram byte is 0xDB, then the sequence 0xDB, 0xDD is transmitted instead.
Using the protocol SLIP requires the fulfillment of a number of conditions:
1. Each exchange partner should know IP-the address of your addressee, since there is no method for exchanging this kind of information.
2. SLIP Unlike Ethernet does not use checksums, so error detection and correction falls entirely on the upper-level software.
3. Since the frame SLIP does not have a type field, it cannot be used, unlike Ethernet frames, to implement other protocols using the encapsulation method.
For the first time protocol SLIP was implemented in 1984 in 4.2 BSD. Information transfer rate when using the protocol SLIP does not exceed 19.2kb/s, which is usually sufficient for interactive exchange within the framework of the telnet or RLOGIN. Maximum transmission block size ( MTU) For SLIP lies close to 256-512 bytes, which provides a reasonable compromise between the response latency (~256ms.) and channel efficiency (~98% for CSLIP). In this case, to transmit one character (pressed key), 20 bytes of header are used in IP-datagram and 20 bytes TCP-heading. If we take into account the costs of formation SLIP-frame, the overhead exceeds 40 bytes.
This drawback has been partially eliminated in new version CSLIP (Compressed SLIP, RFC-1144, proposed by Jacobson in 1990). IN CSLIP the header is reduced to 3-5 bytes (versus 40 in SLIP). This version of the protocol can support up to 16 TCP- connections at each end of the serial channel. Many modern SLIP-drivers support and CSLIP.
PPP (Point-to-Point Protocol)
One of the reasons for the small number of communication channels IP with a direct connection there was a lack of a standard protocol for generating an Internet data packet. Protocol Point-to-Point Protocol (PPP)(Direct Link Protocol) was intended to solve this problem.
In addition to solving the problem of generating standard data packets Internet IP in channels with direct connection, RRR also had to solve other problems, including address assignment and management IP, asynchronous (start/stop) and synchronous bit-based packet generation, network protocol multiplexing, link configuration, link quality testing, error detection and variant negotiation for capabilities such as network layer address negotiation and information compression negotiation.
RRR addresses these issues by providing an extensible Channel Control Protocol ( Link Control Protocol (LCP) and families of Network Management Protocols (Network Control Protocols) (NCP ) , which allow you to negotiate optional configuration parameters and various capabilities.
Today PPP, besides IP, also provides other protocols, including IPX And DECne .
Unlike SLIP- protocol RRR can work through any interface DTE/DCE(For example, EIA RS-232-C, EIA RS- 422, EIA RS-423 and CCITT V.35).
Protocol PPP is quite unpretentious and can work without modem control signals (such as Request to Send, Clear to Send, Data Carrier Detect And Data Terminal Ready). The only absolute requirement that makes RRR, is the requirement to provide redundant circuits (either dedicated or switched) that can operate in either synchronous or asynchronous bit-sequential mode, transparent to link-layer data blocks RRR.
RRR does not impose any restrictions regarding the speed of information transfer, other than those determined by the specific interface used DTE/DCE.
The main difference between the SLIP and PPP protocols from the protocols discussed above is that they support point-to-point communication when network cable used to transfer information only between two computers (or other network equipment) connected by this cable. This connection is typical when connecting to the Internet via a telephone line, when connecting local networks among themselves over leased or dial-up lines, as well as in X.25 networks, Frame Relay and ATM (see later in lectures). Exists a large number of link layer protocols for point-to-point connections, but here we will limit ourselves to considering only SLIP and PPP.
SLIP (Serial Line IP) is a link layer protocol that allows you to use a serial data line (telephone line) to communicate with other computers via IP (network layer protocol). SLIP appeared quite a long time ago for communication between Unix computers over telephone lines and is currently obsolete, because does not allow the use of network layer protocols other than IP, does not allow negotiation of IP addresses of the parties, and has a weak user authentication (identity confirmation) scheme, which consists of sending the user name and password over the network. This way, the username and password (even encrypted) can be intercepted and reused by the attacker, or he can simply wait until the user will be authenticated, and then disable it and connect on behalf of the user. Therefore, most Internet providers use the PPP protocol to connect to their machines.
The link layer protocol PPP (Point to Point Protocol) allows you to use not only the IP protocol, but also other network layer protocols (IPX, AppleTalk, etc.). This is achieved due to the fact that each message frame stores not only a 16-bit checksum, but also a field that specifies the type of network protocol. The PPP protocol also supports compression of IP packet headers using the Van Jacobson method (VJ compression), and also allows you to negotiate the maximum size of transmitted datagrams, IP addresses of the parties, etc. Authentication in the PPP protocol is two-way, i.e. each party may require authentication of the other. The authentication procedure follows one of two schemes:
a) PAP (Password Authentication Protocol) – at the beginning of the connection, the username and
(possibly encrypted) password.
b) CHAP (Challenge Handshake Authentication Protocol) – at the beginning of the connection, the server sends a random request (challenge) to the client. The client encrypts its password using a one-way hash function (a function whose Y value cannot be used to determine X) and a challenge as the encryption key. The encrypted response is sent to the server, which, having the client’s password in its database, performs the same operations and, if the response received from the client matches the one calculated by the server, then authentication is considered successful. Thus, the password is not transmitted over communication lines. Even if the client's response is intercepted, it will not be possible to use it next time, because the server request will be different. It is impossible to determine the password based on the response, because The hash function encrypts data one way only. To prevent interference with the connection after the client has been authenticated, in the CHAP scheme the server regularly sends test requests at regular intervals. If there is no response or an incorrect response, the connection is terminated.
OSI model. Upper levels
The SLIP (Serial Line IP) protocol became the first de facto industrial standard that allowed devices connected by a serial low-speed communication interface to operate over TCP/IP protocols. This Internet protocol allows the use of ordinary telephone lines as communication lines. The protocol was created in the early 80s and, according to RFC-1055, was first included as a means of accessing an IP network in the 3COM package - UNET. In 1984, SLIP was built into the 4.2 Berkley Unix operating system by Rick Adams. SLIP was later supported in other versions of Unix and implemented in software for PC. Due to its functional simplicity, SLIP was and is used mainly on switched communication lines, which are not typical for responsible and high-speed network connections. However, a switched channel differs from a non-switched one only in lower quality and the need to perform the subscriber calling procedure, so SLIP is quite applicable on dedicated channels. The SLIP protocol performs a single function - it allows the stream of bits that arrive over a dedicated (or switched) channel to recognize the beginning and end of an IP packet. SLIP does not support other network layer protocols. Software that implements the SLIP protocol receives characters coming from a serial data device (modem, serial port, etc.); considers and interprets them as components of an IP packet; puts the received data into a full-fledged normal IP packet and transmits this packet further to the appropriate program that processes IP packets, for example, the TCP module. On way back SLIP receives from a program (network layer) sending IP packets, IP packet, extracts its contents, reformats it accordingly, then divides it into characters and sends it through a serial device over a serial line to the network - a neighboring Internet node. SLIP protocol frame structure. The SLIP protocol is designed to transmit IP packets over asynchronous communication lines. Since asynchronous transmission is byte-oriented, before transport by SLIP, the packet is divided into octets (bytes), which are transmitted one after another. As is known, in Ethernet networks An IP packet can be up to 1500 bytes long, which necessitates its segmentation - breaking it into shorter packets. SLIP does this quite primitively. It does not parse the data stream or highlight any information in that stream. To recognize the boundary of IP packets, the SLIP protocol provides for the use of a special character END, the value of which in hexadecimal representation is (C0) A. To separate SLIP frames, a service separator byte is inserted between them - the character ESC (DB) A. The use of a special character can create a conflict: if the byte of the transmitted data is identical to the END character, then it will be erroneously identified as a sign of the end of the packet. To prevent such a byte found inside an IP packet from being perceived as a delimiter, a byte staffing mechanism is provided. Thus, the actual service information in the SLIP protocol is quite small: one separator byte is added per IP packet (they are not duplicated between packets), and sometimes several additional bytes appear, inserted using the byte insertion procedure.
The standard does not define a fixed size for a SLIP frame, so any SLIP interface has a special field in which the user must specify this length. However, in specific implementations the maximum size of a SLIP frame is often limited to a very small value (from 256 to 1006 bytes). This limitation dates back to the first implementation of SLIP in the corresponding Berkley Unix driver, and is necessary to maintain compatibility between different SLIP implementations (most modern implementations support this length and allow the administrator to set its size, and default to 1500 bytes). In each of the SLIP frames, the IP header of 20 bytes is reproduced in full (Fig. 5.11). Because of this, the redundancy that occurs when transmitting long packets over the SLIP protocol is quite large.
The redundancy generated by the asynchronous transmission method itself on the PC-modem interface is also significant (minimum 20% for additional start and table bits for each byte). But nothing can be done about this, since everything personal computers have only asynchronous ports. To establish communication using the SLIP protocol, computers must have information about each other's IP addresses. The SLIP protocol does not have mechanisms that provide the ability to exchange address information, since the frame structure does not provide for an address field and its special processing. Therefore, computers communicating via the SLIP protocol must be assigned IP addresses in advance. Each time a SLIP connection is established, the computer turns into a full-fledged Internet host with its own IP address. If the provider uses dynamic assignment of IP addresses, then with each new connection the computer will receive a new IP address. Consequently, other computers on the network will be forced to look for it under an unknown address. Another disadvantage of the SLIP protocol is its lack of indication of the type of protocol whose packet is encapsulated in the SLIP frame. Therefore, traffic of only one network protocol can be transmitted through a serial line using the SLIP protocol. SLIP does not differentiate between packets based on protocol type, such as IP or DECnet. When working over the SLIP protocol, it is assumed that only the IP protocol is used, as defined by its name Serial Line IP. When working with real telephone lines, which are noisy and therefore distort information during transmission, error detection and correction procedures are necessary. The SLIP protocol does not provide for such procedures. These functions are provided by the underlying protocols: the IP protocol tests the integrity of the packet using the IP header, and one of the two transport protocols (UDP or TCP) checks the integrity of all data using checksums. Standard SLIP does not provide data compression, but there are variants with compression, for example C SLIP. Most modern modems that support V.42bis and MNP5 standards perform this operation in hardware. The low bandwidth of serial communication lines makes it possible to reduce the transmission time of packets, reducing the amount of service information contained in them. This problem is solved using the Compressed SLIP (CSLIP) protocol, which supports compression of IP packet headers. The CSLIP protocol was created at Lawrence Berkeley Labs (LBL) by Van Jacobson as a means to improve the serial transmission efficiency and service level of applications using TCP/IP over slow lines. The CSLIP protocol, compared to the SLIP protocol, uses six times less redundant information (in the form of headers). At low data transfer rates, this difference is noticeable only when working with IP packets carrying small amounts of information; such packets are formed, for example, when working telnet or rlogin. At high speeds, CSLIP gives less gain and almost no gain for packets with large volumes data, for example ftp packets. The appearance of CSLIP explains the fact that when using programs such as telnet, rlogin and others, in order to send one byte of data, 40 bytes of service information must be sent. Header compression replaces the 20 octets of the IP header and 20 octets of the TCP header (40 bytes total) with 3-7 octets. CSLIP uses information from the previous packet to compress, decompress and verify that the packet (and header) has been correctly forwarded, i.e. transmission has a chain structure. The first packet in the chain is uncompressed. If any packet is lost, then the chain is broken, the same packet cannot be requested at the very end of the transmission, it must be resent immediately, i.e. stop the transfer process and start a new chain. Thus, this technology, when packets are lost or corrupted, results in greater time losses than conventional SLIP. This occurs due to delays in stopping and transmitting a new uncompressed packet. Since the SLIP protocol does not provide error detection and correction procedures, it is undesirable to use the UDP and SLIP datagram protocol together. This is because the UDP protocol does not necessarily use checksums. Further development The SLIP protocol is the PPP protocol (RFC 1331), which eliminates some of the shortcomings of the SLIP protocol. It must be remembered that SLIP and PPP are link layer protocols.
SLIP protocol
The SLIP (Serial Line IP) protocol was the first de facto standard that allowed devices connected by a serial line to operate over TCP/IP protocols. It was created in the early 80's and built into 1984 by Rick Adams. operating system 4.2 Berkley Unix. SLIP was later supported in other versions of Unix and implemented in PC software.
True, due to its functional simplicity, SLIP was and is used mainly on switched communication lines, which are not typical for critical and high-speed network connections. Nevertheless, a switched channel differs from a non-switched one only in lower quality and the need to perform the subscriber calling procedure, so SLIP is quite applicable on dedicated channels.
The SLIP protocol performs a single function - it allows the stream of bits that arrive over a dedicated (or switched) channel to recognize the beginning and end of an IP packet. Apart from the IP protocol, SLIP does not support other network layer protocols.
To recognize the boundaries of IP packets, the SLIP protocol uses a special character, END, whose hexadecimal value is C0. The use of a special character can create a conflict: if the byte of the transmitted data is identical to the END character, then it will be erroneously identified as a sign of the end of the packet. To prevent this situation, a data byte with a value equal to the value of the END character is replaced by a composite two-byte sequence consisting of the special character ESC (DB) and the DC code. If the data byte has the same code as the SLIP ESC symbol, then it is replaced by a two-byte sequence consisting of the SLIP ESC symbol itself and the DD code. After the last byte of the packet, the END character is transmitted.
The mechanism of formation of compound sequences is shown in Fig. 6.13. Here are a standard IP packet (one byte of which is identical to the END character, and the other to the SLIP ESC character) and the corresponding SLIP packet, which is 4 bytes larger.
Rice. 6.13. Encapsulating IP packets into SLIP packets
Although the SLIP protocol specification does not define a maximum transmission packet length, actual size An IP packet must not exceed 1006 bytes. This limitation is associated with the first implementation of the SLIP protocol in the corresponding driver for Berkley Unix, and its compliance is necessary to maintain compatibility between different SLIP implementations (most modern implementations allow the administrator to set the packet size themselves, and the default size is 1500 bytes).
To establish communication using the SLIP protocol, computers must have information about each other's IP addresses. However, it is possible that, say, when making a connection between a host and a router, the latter will need to transfer information about its IP address to the host. The SLIP protocol does not have mechanisms that enable the exchange of address information. This limitation prevents the use of SLIP for some types of network services.
Another disadvantage of SLIP is the lack of indication of the type of protocol whose packet is encapsulated in the SLIP packet. Therefore, traffic of only one network protocol - IP - can be transmitted via a serial line using the SLIP protocol.
When working with real telephone lines, which are noisy and therefore distort packets during transmission, error detection and correction procedures are required. The SLIP protocol does not provide for such procedures. These functions are provided by the underlying protocols: the IP protocol tests the integrity of the packet using the IP header, and one of the two transport protocols (UDP or TCP) checks the integrity of all data using checksums.
The low bandwidth of serial communication lines forces us to reduce the transmission time of packets, reducing the amount of service information they contain. This problem is solved using the Compressed SLIP (CSLIP) protocol, which supports packet header compression. The emergence of CSLIP is explained by the fact that when using programs like Telnet, Riogin and others, to send one byte of data, you need to send a 20-byte IP packet header and a 20-byte TCP packet header (a total of 40 bytes). The CSLIP specification allows a 40-byte header to be compressed into 3-5 bytes. Currently, most implementations of the SLIP protocol support the CSLIP specification.
