Onion browser tor. Tor Browser Bundle for safe and anonymous browsing of the Internet


Privacy settings
Tor Browser 7.0.6 in Russian for Windows
To maintain complete anonymity on the Internet, there are different ways, but, as a rule, for this it is necessary to install 1-2, or even more programs, add-ons, etc. Tor Browser, which can be downloaded for free, already includes everything you need. The browser is based on another popular Internet browser, Mozilla Firefox.
Tor provides its users complete anonymity, which means establishing the location, real IP or which sites are viewed in this moment- impossible. In addition, after the session ends, the browser clears all history, cookies and other files, so that no traces remain. The program gives all this for free, you just need to download Tor Browser and install it on your computer.
Thanks to the Tor browser, you can access any sites and resources, for example, those that are blocked in your country. The built-in Vidalia utility will help you do this, in which you can change IP, manage the current session, and also enable traffic relaying so that no one can track you.
It is worth listing the main advantages of the program:
- Complete anonymity when surfing
- Complete Russification of the browser
- Portability, i.e. no need to install
- Availability. Tor Browser can be downloaded absolutely free
- Nice interface
But there are also several significant disadvantages:
- Slow connection speed
- Lack of protection. Since Tor is used not only ordinary people, but also, for example, hackers, then we can say that all “doors” are open for them.
For anonymous web surfing. Represents a web- Firefox browser with an integrated Torbutton extension, a script blocker and an add-on for logging into sites via the HTTPS protocol.
The program allows you to visit sites prohibited by the administrator or the state, as well as correspond in web chats, place orders and download files, hiding your IP address and other identification elements.
A proxy server system called “Tor” was created by employees of the US Navy Research Laboratory. After the US Department of Defense decided to declassify the project, transferring it to Open Source(open source), a group of independent developers took on its development. As a result, more than 6,000 communication nodes have appeared on various continents, providing data transmission in super-encrypted form through anonymous proxies. Tor servers.

The application works without installation. That is, you can download it to your computer, and then copy it to a USB device and run it on another PC.

After launch, a slightly redesigned Firefox browser opens. It is almost no different from standard browser except that it allows you to surf the Internet anonymously - using encrypted virtual tunnels between Tor communication nodes. Thus, the user receives the long-awaited opportunity to access sites that were previously blocked at the level of the employer company, Internet provider, or even the state. Moreover, neither other users, nor bots, nor special utilities will not be able to track his location or “read” any data about his laptop or desktop PC.
Possibilities:
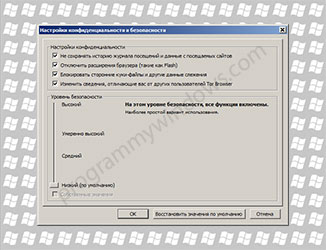
- protection from online surveillance;
- blocking flash content, which is often a security threat;
- auto-delete cookies, history and cache in the browser;
- hiding hardware configuration from visited hosts;
- forced use of the HTTPS protocol.
Advantages:
- it is possible to download Tor Browser in Russian;
- does not require special settings— ready to use after launch;
- provides access to prohibited sites;
- guarantees privacy on the Internet;
- Tor Browser launches without installation (including from a flash drive or memory card).
Things to work on:
According to the developers, Russia ranks third in the number of users who have installed Tor. The Russian version of Tor Browser will be understandable even to not very experienced users. You can work with the browser immediately after launching - for anonymous surfing everything is already provided for.
The program is intended for users who want to protect privacy, ensure the confidentiality of Internet surfing, and also gain access to web pages prohibited by Internet censorship. Allows you to create websites or blogs without disclosing the location of the authors.
If you are tired of the feeling of prying eyes watching you in order to sell something, then it’s time for you to find out what the Tor browser is.
Personal information left by the user in in social networks, online stores, on the websites of government organizations and simply in search engines, I am very interested primarily in the same search companies. They process user preferences to improve their algorithms and improve the quality of search results.
In addition, hungry attackers are prowling the depths of the Internet, wanting to gain access to your data. bank cards and electronic wallets.
Marketers also contribute to monitoring your movements on the Internet: it is very important for them to find out what can be sold to you based on the queries that you continue to type into search engines. You just have to log in Mailbox, and there are already very important offers to go there and buy something, having previously studied in such and such courses, not free, of course.
One can only assume, but, most likely, the intelligence services are also interested in your information, at least from the position of total control over the population, of course, for the sake of national security. After summarizing all of the above, there is a natural desire to avoid such dense attention surrounding simple user Internet networks. And this is precisely the opportunity that the Tor browser can provide you with.
The Onion Router
So what is tor? TOR browser is free and open source software, the name of which is an acronym for The Onion Router, and in Russian: onion router, or onion router. The name of the browser reflects the basic principles on which its encryption system, written in languages Python programming, C and C++. In general, the system is a network of proxy servers that establish an anonymous connection in the form of a virtual tunnel, in which it is impossible to calculate the user’s location, since data transmission is encrypted.
Through the use of an extensive system of servers, or information nodes, this browser allows the user to remain anonymous, invisible to all potential scammers, robbers, spies and other users with reduced social responsibility. With its help, you can create your own websites without advertising their location, and you can also contact those sites that are blocked by official censorship.
Mike Perry, one of the developers of Tor, believes that the browser can provide a high level of protection even from such spyware, like PRISM.
History of appearance
Tor Browser was largely created at the US Navy Research Laboratory while US intelligence agencies were working on the Free Heaven project. For some unknown reason, the project was closed, and all source codes Got into public network, where talented programmers caught them and organized the Torproject.org community. Here the browser has already been finalized by volunteer developers, although it continues to be improved, developed and updated to this day.
Just a year ago, Tor already had more than 7,000 system nodes installed on all continents of the Earth, excluding Antarctica, and the number of network users exceeded 2 million. According to Tor Metrics statistics, in 2014, Russia joined the top three countries using the Tor browser most actively. Since the browser is an open-source system that various programmers have worked on for more than 15 years, you don’t have to worry that it may turn out to be a tricky one, and instead of protecting information, it will steal it.
Exactly open source browser gives us a guarantee of the safety of its use.
Video review of the browser, a little history and main purpose
How the system works
The existing TOR technology allows any user to access any website without leaving any traces behind. That is, on the site you visited, they will not be able to track the IP address of your computer, which means they will not be able to identify you. This will not be available even to your Internet provider. And the browser itself will not store information about your movements on the Internet.
The operating principle of the bulbous system can be represented as follows:
1. Communication nodes are formed and installed in different countries apologists for this technology. 3 random nodes are used to transmit data, but no one knows which ones. The data that users transmit is encrypted multiple times, with each level of encryption being another layer of the onion router package. It should be taken into account that only the path, or routing, is encrypted, and not the contents of the information packets themselves. So if you want to secret information reached the recipient completely intact, additional encryption will be required.
2. At each subsequent node through which a packet of information is transmitted, one layer of the cipher is decrypted, containing information about the next intermediate point. After reading this information, the used layer of the onion is removed.
That is, the browser transmits a packet to the first node that contains the encrypted address of the second node. Node No. 1 knows the key for the encryption and, having received the address of Node No. 2, sends a packet there, which is similar to the peeling of the first layer of onion. Node No. 2, having received the packet, owns the key to decrypt the address of Node No. 3 - another layer of husk has been removed from the onion. And this is repeated several times. Thus, from the outside it will be impossible to understand which site you ultimately opened in your Tor browser window.
Video instructions for installation and configuration
Disadvantages of the system
Search engines, an Internet service provider, or someone else who is already used to monitoring your web surfing may guess that you are using Tor. They won't know what exactly you are watching or doing online, but the fact that you want to hide something will become known to them. Therefore you will have to study existing methods increasing anonymity, if you choose this path.
The Tor system uses simple computers, not high speed. This leads to another drawback: the speed of information transfer in this anonymous network may not be enough to watch, for example, videos or other entertainment content.
Currently, the Tor browser is working and actively developing, using more than 15 languages, including Russian. The latest version of Tor was released on January 23, 2017. In some countries, the Tor Project website is blocked or censored, making it impossible to download the Tor Browser directly. In this case, you can use a mirror: Tor Browser Bundle on Github, but if mirrors are not available, you can try downloading it through the Gettor service.
Don't forget to leave your feedback about the browser
Tor Browser– a browser that ensures the anonymity of your Internet surfing. Tor Browser Russian version combines a specially configured Firefox browser and Tor software. Anonymity of visiting sites is ensured by encrypting traffic and routing through a worldwide network of servers. Thus, tracking of your Internet connection, leakage of any information about the configuration of your equipment is completely excluded, and no host will be able to calculate your physical location.
Initially, the “Tor” proxy server system was developed for the American Navy, but after it was declassified by the US Department of Defense, independent developers became interested in it and created the Tor Browser already known to us in Russian. As a result, we have 6,000 nodes located on all continents that transmit ultra-encrypted information via anonymous proxy servers Thor. By installing the Tor Browser on your computer, you will be able to access any prohibited sites, communicate in web chats, make purchases, download files, and no one will track you down by your IP address.
For Tor works Browser for Windows 7, 8, 10 does not need to be installed. Just download installation file and dump it onto a flash drive and you can run it from any other device. Tor Browser is no different from a regular browser, its interface is similar to that of Firefox. In addition, there is Tor Browser for Android devices that even an inexperienced user can understand.
Main features of Tor Browser for Windows 7, 8, 10:
- Anonymous site visits
- Inability to track a person by IP
- The ability to work in a browser without installing it on your computer
- Availability of a Russian version, making it easier to master the program
- Ability to block Flash content that compromises security
- The browser automatically clears your browsing history, cache, and cookies.
Latest version Tor Browser in Russian language provides anonymity of your visit, but does not insure you against the loss of personal data, so you need to be responsible about security issues.
The Tor Browser Bundle web navigator with unique functionality provides anonymous and secure browsing, protection from IP location tracking, and confidentiality of work and personal contacts. Such unprecedented security measures are possible through the use of onion routing in a volunteer-created distributed network Tor, consisting of private servers. We recommend downloading the Tor Browser for free without leaving https://site from the official website in order to get a convenient and familiar browser for viewing sites with bonuses in the form of security, anonymity and freedom from intrusive aggressive advertising. Permanent link: https://site/ru/browsers/tor
The Tor package is composed of a specifically configured Portable Mozilla Firefox web browser with a set of extensions (Torbutton, NoScript and HTTPS Everywhere) and the necessary utilities. Anonymity, security and freedom are designed to serve all corners of the network of Tor servers with The Onion Router routers, hidden services that create multiple connection points with redirection of clients to different IP addresses, network bridges for masking traffic and their protection Bridge Guard, intermediary, watchdog and exit nodes, relays (Tor Bridges), exit enclaves and other technological advances.
Functional advantages of Thor
Correct connection to Tor networks using Tor Browser Bundle provides complete unlimited access to any information on the network and reliable protection from collecting information from the provider, site owners, spyware, statistics services, analysis. To maintain anonymity and maintain a high level of security on the Internet when visiting websites, viewing html pages, video materials, animations, 3-D content, listening to mp3 albums and Internet radio, communicating on social networks, forums and interactive web projects required anonymous Tor Browser download free Russian version. It is difficult to overestimate the importance of security when it comes to shopping in online stores, online banking, working with others financial applications or web resources and communication using instant messages and email. Creative Internet users will be protected from spying and eavesdropping when blogging, filling web resources with content, and working with online videos. Positive reviews and comments, mutual assistance from users and unique functionality make millions of people pay attention and download the free Tor Browser for free on a computer with Windows XP, Vista, 7, 8, 8.1, 10 (x86 and x64).
You definitely need to know about the following advantages of Tor:
Safe and anonymous browsing,
- ignoring sanctions from providers and operators,
- full access to blocked web resources,
- data transmission in encrypted form,
- prohibition of location tracking,
- arbitrary change of IP address to bypass IP address restrictions,
- prohibition of analyzing the browsing history of visited html pages,
- protection against Internet connection surveillance,
- mixing user traffic to block tracking,
- deleting all Cookies when leaving the Internet,
- making changes to Internet access settings,
- runs on any computer from any media, including USB.
Among the shortcomings it is worth noting high speed the operation of websites and the limited safe interactive functionality of Internet resources. It is also worth remembering that Tor does not protect against information leakage 100%, so you should not ignore standard security methods. Hybrid Tor Network Cannot Completely Ensure Hiding transmitted information and protection against malware and spyware software. For getting high level confidentiality requires secure communications, data encryption, and the use of other security technologies. In particular, it is imperative to download free antivirus, use it constantly and sometimes additionally scan the system one-time utility Dr.Web CureIt! When blocking access to the Tor network, the manufacturer recommends setting up a Tor bridge node. A current list of bridges can be obtained at email by subscribing to the office. newsletter. To do this you will need to send an email [email protected] message with the subject line "get bridges".
How to download Tor Browser correctly
To achieve the maximum level of security, you need to download official browsers from official websites. This applies not only to how latest version Tor Browser Bundle download for free from the official website. This recommendation also applies to other browsers, such as Mozilla Firefox or Google Chrome.
Naturally, and Browser Thor has an official website where you can safely download Tor Browser for free in Russian and 15 other languages for MS Windows, Apple Mac OS X and Linux. For Android you can download the Orbot application for free, which is almost completely similar in functionality. Enthusiasts are also developing the project in operating rooms Unix systems, iOS, FirefoxOS, OS/2 and others. The official website of the Tor browser is torproject in the org domain on English language. By the way, regarding security, the portable Tor Browser Bundle cannot be found on the official website, so it is better not to use it. Everyone who does portable version, they do not do this out of good intentions, because, official browser from the official website suggests the possibility of portable use. Beware of the Portable Tor versions browser available for download on questionable websites is not safe. Be sure to check the source of the file, the download must be done from the developer on torproject in the org domain. On this page this is exactly the case, and you can absolutely safely download Tor Browser for free from the official website without leaving current page https://site without registration.
Which Adobe Flash Player to download
Tor Browser Bundle is based on the Mazila Firefox web browser. To play video, multimedia and web content in Flash format, you will need to download Adobe for free Flash Player for Mozilla Firefox and install it on the system.
