Intel Security True Key: what is this program and how to remove it? Fighting remote control: how to disable Intel ME.
Users have become accustomed to the fact that small, second-rate programs are bundled with the installer of popular software. Among such software, True Key stands out. What kind of program this is, what it is needed for and how to remove it from your computer you can read in this article.
True Key - what is it
Functions
The program is multi-platform and can work in one account from several devices.
Login methods (can be combined) |
|
| Face recognition | A web camera is required. The procedure scans your face, remembers its features and, based on analysis, determines whether to grant access or not. |
| Fingerprint | Requires a fingerprint scanner. |
| Multi-factor authentication | To access the application on a PC, you need to enter a verification code from another device (for example, from a phone). |
| Master password | Application access password. |
| To confirm your login, you need to follow the link. | |
| Trusted device | The program remembers the device you are working from and offers to add it to the trusted ones. If you try to log in from another device, the program will notify you about it. |
Working with information |
|
| Launchpad | After logging into your account, it allows you to conveniently organize your work with websites. |
| Password Manager | Enter the data once and the program will automatically enter it for you. |
| Storing information about cards and accounts | Allows you to store data electronic invoices, plastic cards, passport and other personal data. |
| Password generator | Allows you to generate complex and strong password for guard account or other data. |
| Facial recognition when logging into Windows | A web camera is required. The program allows you not only to store personal data in Windows profile, but also to protect the profile itself. |
| Encryption and synchronization | The information is stored on your device, and when synchronized with another device, the AES-256 encryption algorithm is used. |
The program is not bad, it has a demon paid version, which supports storing 15 passwords. To remove restrictions, you can purchase a paid version for 999 rubles per year.
Intel ME technology (or AMT, Active Management Technology) is one of the most mysterious and powerful elements of modern x86 platforms. The tool was originally created as a solution for remote administration. However, it has such powerful functionality and is so beyond the control of users of Intel-based devices that many of them would like to disable this technology, which is not so easy to do.
Intel ME technology (or AMT, Active Management Technology) is one of the most mysterious and powerful elements of modern x86 platforms. The tool was originally created as a solution for remote administration. However, it has such powerful functionality and is so beyond the control of users of Intel-based devices that many of them would like to disable this technology, which is not so easy to do.
At the Positive Hack Days VI forum held in Moscow on May 17 and 18, Positive Technologies researchers Maxim Goryachiy and Mark Ermolov presented several techniques for disabling Intel ME, accompanying the report with a video demonstration of the process.
What is it and why do you need to turn it off?
The Intel Management Engine (ME) subsystem is an additional "hidden" processor that is present in all devices based on Intel chipsets(not only in PCs and laptops, but also in servers). The ME runtime environment never “sleeps” and works even when the computer is turned off (in the presence of standby voltage), and also has access to random access memory, network interface, USB controller and built-in graphics adapter.Despite such extensive capabilities, there are questions about the level of security of ME - previously, researchers have already found serious vulnerabilities and attack vectors. In addition, the subsystem contains potentially dangerous functions - remote control, NFC, hidden service partition. The ME subsystem interfaces are undocumented and the implementation is closed.
All these reasons lead many to view ME technology as a “hardware hack.” The situation is aggravated by the fact that, on the one hand, the device user does not have the ability to disable this functionality, and on the other hand, the equipment manufacturer may make errors in the ME configuration.
Good news The problem is that there are still ways to disable ME.
Techniques for disabling Intel ME
Positive Technologies researchers Maxim Goryachiy and Mark Ermolov presented a report on disabling Intel ME during the Positive Hack Days VI forum held in Moscow. Experts have described several techniques for disabling this subsystem:- Failure-based ME initialization;
- Through the ME firmware update mechanism;
- Undocumented Commands
- An undocumented mechanism intended for hardware developers - Manufacture Mode.
Most shutdown methods use built-in ME mechanisms designed for device vendors on Intel platform. All of them are described in detail in the presentation, which is published on GitHub. The link provides a demo video of disabling ME (it’s also below):
And yet, a reasonable question arises: “Does ME really stop working fully when using its built-in shutdown mechanisms?” As proof of the fact that ME is disabled, the researchers present the following argument: ME operates in two memory modes: SRAM only (built into ME) and SRAM + UMA. UMA is a part of the host memory that is used as paged memory (swap). Once the DRAM controller is initialized by the host, the ME always switches to SRAM + UMA mode.
Thus, if the ME is really turned off, then when the ME access to UMA memory is disabled at the hardware level at an arbitrary moment (via the VСm channel), hardware failures will not occur in the ME due to the lack of data and code that were forced out into the UMA memory (such hardware failures lead to an emergency power outage from the main hardware components of the platform). On the other hand, the use of these methods makes it possible to carry out DoS attacks on AMT technology if it is used for remote management.
Dear friends, if you found True Key on your computer and don’t know what kind of program it is, then you are in the right place. Today we will look at the functionality this application and find out how to remove True Key from your computer (and is it necessary to do this at all). Adding fuel to the fire is the fact that some antiviruses detect True Key as malicious. software and the user is in a panic looking for answers to all questions.
I won’t pull the cat by the tail and will write right away - True Key is enough interesting program and, most importantly, with fairly good functionality. But the approach to advertising and promoting your product, combined with a fairly large price tag, kills all the advantages and you involuntarily think about an alternative.
True Key Intel Security is the full name of this application for the computer. Such monsters as Intel and McAffe took part in its development, and while I trust the former, I have always avoided the products of the second development participant. This software can be divided into two logical parts:
- The True Key Intel Security application itself is installed like any other program on your computer and is a kind of password manager - all information and settings are made through the application itself;
- Browser extension - responsible for synchronizing the application and browsers. Just install the application, log in, activate the browser extension, and you will automatically log in to all previously saved sites - and this is not only on a computer or laptop, there is also an application for smartphones.

It turns out to be a kind of analogue of synchronizing browsers with each other (they have been able to do this for a long time, completely free), but here one significant minute appears - the program is shareware. For free, you can enter only 15 passwords into the program, do you want more? — pay 900 rubles per year (price current at the time of writing).
The price is relatively small, but considering dampness product and various alternatives - I think we will have to say goodbye to it. Searching for broken versions on torrents is not the smartest solution. I wouldn’t trust all my passwords to an unknown program modified by someone - it’s more expensive for myself. Considering that you most likely came across True Key on your computer completely by accident - even if you want to use it... delete it and download it again from the official website to be safe.
How True Key appears on your system
Each user can visit the official website of the program and download the free version to their computer. Some very harmful antiviruses (Avast for example) may falsely trigger and warn about evil and scary program. In fact, True Kay is not doing anything wrong, but the method of promoting them is simply ACHTUNG.
Wanted to update Adobe Flash Player - receive and sign, you may have set True Key (by the way, did you notice that previously, along with the flash player, it was almost always offered free scanner from McAfee... and who is one of the developers of True Kay?). Have you updated the drivers for the Intel chipset? — be careful, without your knowledge, nothing will most likely be installed on its own. In most cases, you most likely missed the small checkbox, leaving which you agreed to install True Key on your computer.
Thinking out loud: My personal opinion, it may be incorrect, because of such a distribution policy, users simply complained about this program and the software automatically began to be defined as dangerous software. Like Sputnik.Mail, for example, or the Amigo browser - the software doesn’t seem to do anything bad, they even have their own features - but the distribution policy ruins all use in the bud, and even puts users in a negative mood
So, we figured out what the True Key program is. If you haven’t installed it and don’t want to use it, then the question arises: how to remove True Key from your computer? There is nothing unusual here - the application was developed by fairly reputable companies and there cannot be any difficulties here, but just in case we will consider standard way And Alternative option- if something went wrong.
Removing True Key via Application Manager
As I wrote above, the application can be easily removed through everyone’s favorite control panel. Open Add/Remove Programs (in Windows 10 this item is simply called “Programs”) in Control Panel and in the list, find “Intel Security True Key”. Click on the “Delete/Change” button and wait complete removal Tru Kay - after that it is recommended to restart the computer.
How to remove True Key from your computer if the application is not uninstalled
There are situations when the True Key application cannot be uninstalled regular means Windows (this is a wake-up call to think that something is not quite right with your OS), what this is connected with - I cannot say, but test system I could not reproduce this situation (and I didn’t really try). Therefore, I offer you an alternative option for uninstalling the True Key program.
- Call “Task Manager” (I don’t know the spell, so press CTRL + SHIFT + ESC);
- In the list we look for everything related to True Key and complete all these processes. The picture below shows an example from the dispatcher Windows tasks 10;
By doing this, we have unloaded the application from the computer’s RAM and it will no longer interfere with us during uninstallation.

The next step is to use a third party uninstaller (since the standard one let us down). For example I used CCleaner program (I don’t like it, but it will do for our needs)- it will be enough for us free version, there is no need to look for broken and patched ones - everything works right out of the box.
Go to “Tools” - “Uninstall programs” and look for “Intel Security True Key” in the list. Click “Uninstall” and wait until the program is uninstalled. After completion, as usual, restart your computer and use it without the annoying True Key.

Well, we figured out what kind of program this is - True Key and how to remove it from your computer. There shouldn’t be any particular difficulties here - everything is as simple and standard as possible, no more difficult than uninstalling a game or any other program.
P.S. Dear friends, please understand correctly - the True Key application is not bad and is probably worth the money if you cannot remember all your passwords and you don’t mind paying 900 rubles a year to autofill them on all devices. But the methods of getting onto the computer True Kay calls only negative emotions and I want to delete this program as soon as possible (We just got acquainted with the True Key removal methods in this article)
Probably none of the computer or computer users mobile systems no need to say that today on the same Internet, access to many services, services or sites requires entering a login and password. But you won’t remember them all. And keep the data on the computer in the same form text file, and even in unencrypted form, is a very dangerous matter. One solution to this problem is the Intel Security True Key program. It was developed jointly by Intel and MacAfee. So why do many users who have actually tried it try to get rid of this application?
True Key: what is this program?
The True Key application is positioned as a reliable utility that allows you to store logins, passwords and any other user registration data not on personal computer or laptop, and on remote server.
In addition, there is one more aspect of the True Key application worth paying attention to. What kind of program this is in terms of security of access to secret data is not difficult to understand if you look at the capabilities of its system for storing confidential information. Naturally, there is complete encryption of information, the ability to synchronize between several accounts, and trusted device for login, etc.
Why do you need the True Key program: security issues
In terms of protecting data from unauthorized use, the application offers not only standard methods. For example, in addition to encrypting and establishing secure communication channels, the program allows you to identify a user by fingerprint or even by matching facial features.
Thus, protection seems to be provided in fact high level. However, the registration data is saved not on the local terminal, but, as already mentioned, on a remote server, which increases the user’s chances that his information will not be stolen.

However, not all so simple. Now another look at the True Key app. What kind of program this is is already a little clear, let’s move on, so to speak, to the commercial side. The fact is that the application itself is shareware. Why "as if"? Only because the free version supports up to 15 passwords. If there are more of them, you will have to fork out for a premium account, which will cost about 20 US dollars.
Why is there a need to remove it?
Now the most main question: “Why are some users trying to get rid of such a seemingly necessary and advanced application?” (how to remove the True Key program using several methods will be discussed a little later).
Here, according to many users and experts, the problem is that the application developers have clearly gone too far with advertising, and some authorization methods look very inconvenient. In addition, the program gets onto some computers spontaneously. This happens either if there are update utilities on the computer Intel drivers, or through installing other applications as affiliate program, or in the form of a virus masquerading as official utility. In the latter case, the user receives a browser hijacker, making it difficult to search, changing start pages that adds advertisements, redirects him to commercial or dubious sites and steals personal information. And this option has nothing to do with the official application.
Standard procedure
So, let's see how to remove the True Key program the most simple method using OS tools for this. Let’s make a reservation right away: the application is cross-platform, and different systems The methodology may vary, so here are the removal methods for Windows.
Let’s say the user is faced with a series of acute questions: “What is this – True Key?” and “How to remove a program?” Let's assume that he has already figured out the first one. We need to find the answer to the second one.

The solution to the problem is standard for all Windows systems. To uninstall an application, use the programs and components section in the Control Panel, where you just need to find the program itself and perform a standard uninstallation. But that is not all.

After this you need to enter the editor system registry(regedit in the Run console), search by name and delete all keys corresponding to the application. But this way you can remove something that is not at all what is required.
Therefore after standard removal better use CCleaner utility or similar, which will find all outdated or unused keys and delete them without user intervention.
Using highly targeted utilities
Another solution could be to use programs like iObit Uninstaller. Its interface is somewhat reminiscent of the program section window and Windows components, so it won’t be difficult to find the program in the list.

In this case, the standard uninstaller will first be launched, after which a search will occur residual files and registry keys. All this garbage will also need to be removed, and using the file destruction line on the hard drive. If for some reason the application does not appear in the list, it can be removed using the Forced Uninstall module with a preliminary search.
What to do if it's a virus?
Finally, a few more words about the True Key application. What kind of program this is in the original is already clear. But if, after installation, suspicions arise about a virus with the symptoms described above, you should first use not the one installed on the system, but some third-party portable utility, and if the threat is not identified, apply the listed steps for manual removal.
Note: in all cases, first in the “Task Manager” you need to forcefully terminate all processes associated with the program, remove the application module from startup, and it is advisable to remove it while booting the system into safe mode(required only for cases of viral infection).
 Hello everyone, now I will talk about what kind of program Intel Security True Key is. But the fact that the program name contains the word Intel is already encouraging. Well, that is, I think you understand what I mean; I personally have long associated the word Intel with quality. But I don’t want to offend anyone, well, who doesn’t like this company, this is just my opinion. I like Intel, but I wouldn't give it up AMD process, which has 8 cores and a TDP of 125 W! This is a good eight-core affordable price! But what am I talking about? I got a little distracted, so sorry...
Hello everyone, now I will talk about what kind of program Intel Security True Key is. But the fact that the program name contains the word Intel is already encouraging. Well, that is, I think you understand what I mean; I personally have long associated the word Intel with quality. But I don’t want to offend anyone, well, who doesn’t like this company, this is just my opinion. I like Intel, but I wouldn't give it up AMD process, which has 8 cores and a TDP of 125 W! This is a good eight-core affordable price! But what am I talking about? I got a little distracted, so sorry...
Let's go back to Intel program Security True Key. This means that this program was the first to appear on smartphones and tablets from Prestigio. I can’t say that I really like this company, somehow it doesn’t inspire confidence...
Well, Intel Security True Key is positioned as a program that will save you from passwords; you no longer need to remember them, come up with them, and all that. The trick is that instead of passwords, a face, fingerprints, foot size, or something similar will be used. As for me, this technology has been around for a long time and it has also been in a damp state for a long time, well, everyone is used to passwords, including me, and I don’t know how long it will take for the world to switch from passwords to fingerprints. And it’s unlikely that everything works in practice without glitches...
So these are the things, but of course the good news is that this program is from Intel, that is, it might be worth trying, but the question about convenience remains open.
Intel Security True Key: Debriefing
Well, I downloaded this program to my computer to see what it was all about.
In general, I’m starting to install, here’s a beautiful installer:

And now the installation has begun, everything is also beautifully decorated:

It also seemed like some McAfee components were installed... Although I didn’t see it written to me anywhere that they would also be installed. Well, okay, I think, McAfee is also from Intel anyway..
Everything was installed for about a minute, then I clicked the Continue button and the True Key program opened, this is what it looked like:

As for me, Hello could have been written less. I clicked Get Started and was prompted to create a free True Key profile:
Well, you know, I didn’t do this, well, I was already too lazy.. I was just wondering what kind of program it was, but in order to start using it, you need to register in it, that’s how it goes
By the way, here’s what else I thought, I read that instead of a password, a facial contour can be used. That is, with age, this contour may cease to be perceived? Or, for example, you have a bruise there, or something else, in short, there’s a bandage on your head. So that’s it, you no longer log in to the site using True Key? Well, I do not know. But as I already wrote at the beginning, all this is still very crude and inconvenient; I think they will continue to use passwords for a very long time, although it is unlikely that they will completely abandon them...
In general, these are the things. Now we need to see what this program actually puts into Windows, so to speak, what kind of things it adds to Windows. So I rebooted, the tray icon was no longer there, I thought that probably the Intel Security True Key did not load with Windows, but if only I knew how wrong I was!
So I opened the task manager and this is what I see there:

As you can see, there are a lot of processes here, and there are even processes from McAfee.
So let’s go figure it out, the McAfee.TrueKey.Service.exe process is launched from this folder:
C:\Program Files\TrueKey

It turned out that McTkSchedulerService.exe and McAfee.TrueKey.ServiceHelper.exe are also launched from that folder.
The pabeSvc64.exe process, which is generally similar in name to a virus, is launched from this folder:
C:\Program Files\Intel\BCA

In general, as you can see, there are a bunch of processes. But I seem to understand why I was not informed that McAfee components would also be installed, as I understand, they are needed for the True Key program itself to work. After all, McAfee is something like an antivirus, I don’t remember exactly, but I know exactly what relates to security. That is, True Key and McAfee are security programs from Intel, so the fact that McAfee components are installed only means that the True Key program uses security features from McAfee. Well something like this
Look, in this folder:
C:\Program Files
After installing True Key, three folders appeared (and you may have more):

At the same time, what’s interesting is that the True Key program itself runs under the truekey.exe process and is installed in this folder:
C:\Program Files\Intel Security\True Key\application

And here in this folder:
C:\Program Files (x86)
The McAfee folder appears:
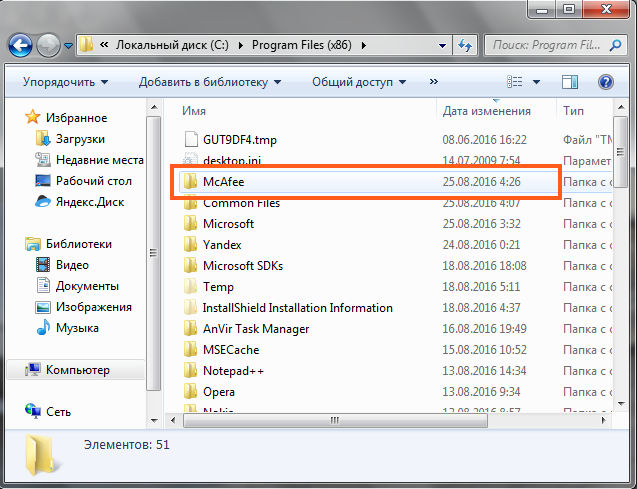
But it was empty, I don’t know why it was created...
It’s strange, but in startup I didn’t find anything from either the True Key program or McAfee, and I think I know why... New services have probably appeared that perform the task of autostarting the program.. In general, I’m going to have a look..
I open the task manager, go to the Services tab and click the button with the same name there:
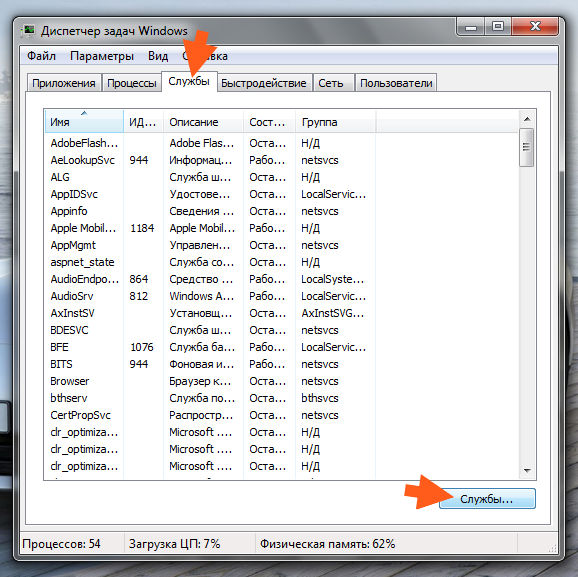
A window with services opened. Well, what needed to be proven, here I found four services, these are Intel Security True Key, Intel Security True Key Scheduler, Intel(R) Biometric and Context Agent Service and TrueKeyServiceHelper, here they are all:

Maybe you will have more of these services, but I have only so many. Yes, so to speak, there are quite a lot of services, of course. The True Key program, as we see, is well integrated into the computer!
So let's go through each service. That is, I’ll double-click on each one to understand what the process is and where it starts from. Here is the Intel Security True Key service (sort of like the main service):

Here is the Intel Security True Key Scheduler service (obviously something related to the scheduler):

Here is the Intel(R) Biometric and Context Agent Service (related to biometrics and something else):
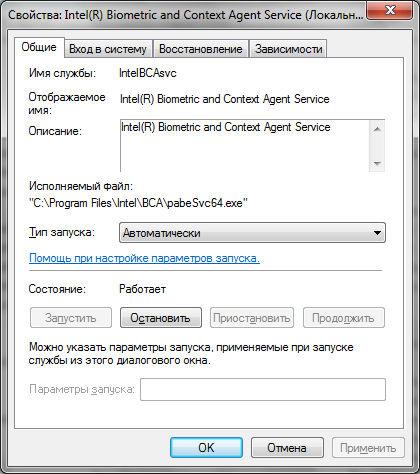
Well, the TrueKeyServiceHelper service (this already applies to support or help):

These are the things, of course, what can you say, it’s pretty bad. Four services, as for me, is already too much, but this is my opinion...
If you want to disable a service, just double-click on it in the list, then where Startup Type is, select Disabled and click the Stop button. This way you will turn it off completely. But it’s possible that the True Key program will turn it on again later.. This is life guys.. You need to be able to survive..
How to completely remove True Key from your computer?
Yes, if True Key got onto your computer by accident, then I understand why you want to delete it. After all, it is well embedded in the computer, right from the roots, and processes and folders and services, this is already too much. It's better to remove it completely!
