What are proprietary protocols? Data transmission in portable multimedia players: proprietary protocols
The main difference between portable audio players of the “Internet generation” and their predecessors is their close integration with a personal computer.
In the past, portable players played music from common removable media and did not need to be connected to anything other than headphones
Until recently, the PC was their only source of content. At the same time, there was a need for a mechanism for pairing a portable player and a computer. The task was to transfer data in digital form from one medium (in a PC) to another (in a player) in a format accepted in the computer industry.

Content must be transferred from the computer, where it is usually stored on a 3.5" hard drive, to portable media players: flash memory, 1" and 1.8" hard drives.
Therefore, some kind of computer data interface must be used.
In any such interface, two levels can be distinguished. The first is physical, i.e. directly wires, connectors, microcircuits, etc. The second is software, which is, relatively speaking, a set of instructions and algorithms according to which data is exchanged at the physical level. This software layer is often called a protocol. Today we will mainly talk about it. For the user, it is the “face” of the interface; its capabilities and disadvantages determine the convenience or difficulty in operating the device as a whole.
To fully operate the protocol, two software components are required. Firstly, this is a driver that directly connects a portable device and a PC at the software level. Secondly, it is software that allows the user to manage the protocol and use it for their needs. Software, strictly speaking, is not a direct part of the protocol. But without its presence, the very existence of the protocol becomes meaningless. Therefore, in this article we will consider software as an integral part of the protocols under consideration.
Any software protocol uses drivers and software, although the implementation of these components in each specific case may vary greatly. The success of the protocol can be roughly calculated using the formula: opportunities minus inconveniences. Capabilities refer to the range of available functions. Disadvantages usually include opacity to use, inconvenient installation, difficulty to learn, and limited compatibility.
By the standards of digital portable technology, MP3 players are already a fairly old class of devices. They appeared at a time when the PC infrastructure was completely unprepared for the computer's role as a multimedia host. Both at the physical and software levels, there were no widespread and standardized solutions in this area; they were only in development, preparing to enter the market, or existed in piece quantities. Other related classes of portable devices found themselves in a similar position: mobile storage devices, digital cameras, cell phones, PDAs. All these types of mobile technology appeared at approximately the same time, in the second half of the 90s. Their appearance necessitated the development of unified standard protocols for pairing PCs with portable equipment.
On the physical level, everything was relatively clear. The first portable devices were forced to use COM and LPT - there were simply no other widely available interfaces at that time.

The LPT connector can still be found on most PCs
Thus, it was the LPT physical interface that was used by the founders of MP3 players, Saehan MpMan and Diamond Rio. This period can be called “handicraft”; developers had to use interfaces and protocols that were originally created for completely different tasks.
However, the new generation of portable audio did not have to suffer for long in the shackles of slow and inconvenient interfaces: already in the next 1999, manufacturers introduced a wide range of devices using the new standard: USB, Universal Serial Bus.

For some time, there was a semblance of a struggle between USB and the Firewire protocol, common mainly on Apple Macintosh computers.

WarFirewire-USB in portable players: fromiPod 1G – onlyFirewire - up toiPod 5G – onlyUSB
However, the bulk of portable audio quickly and painlessly switched to the Universal Serial Bus, closing, at least within the framework of wired solutions, the issue of data transfer at the physical level.
Things didn't work out so simply for software protocols. During the short period when manufacturers were forced to use COM and LPT, the software protocols were exclusively of their own design. In fact, they couldn’t be anything else, because... Both COM and LPT interfaces were created at one time, naturally, not at all for transferring multimedia files to portable digital players. There was no one to develop drivers and software shells for the latter except the developers themselves, and there was no talk of standardization at all.
But the advent of USB did not solve the problem. The industry is primarily concerned with creating standard protocols for mobile storage devices and digital cameras. The situation with MP3 players was not at all clear: would they be banned or not, and if they were not banned, then what features should the protocols have for the SDMI forum to give the go-ahead. In such conditions, the development of software protocols still fell on the shoulders of the device developer. This went on for at least four years, until, finally, standard data transfer protocols began to appear in players. These years were the time of dominance of the first type of software protocols - proprietary or closed.
Their characteristic feature was individual drivers and software for each manufacturer, and often for each new generation of players within the products of the same manufacturer.


Proprietary protocol as an exampleRCA-ThomsonLyra. Uses its own driver (PDP2222.SYS), which must be installed separately on each PC to which you plan to connect the player
This creates a lot of inconvenience for the user. There is no talk of any transparency - the user himself is forced to manually install drivers and software for his player. In this case, various difficulties may arise, for example, if the buyer mistakenly connects the player to the PC before installing the drivers.
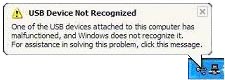
Having mixed up the procedure for connecting the player, the user risked admiring a similar message, even after subsequently installing all the necessary drivers
It’s also better to forget about compatibility: drivers and software only worked with a given player model (at best, with several models from a given manufacturer), and the player could only work with a PC on which these drivers and software were installed. At first, the capabilities of software shells were very meager and were limited exclusively to copying audio files into the player’s memory. Later, a variety of ways to copy content to the player appeared: individually by track or by synchronizing the contents of the player’s memory with the contents of a library compiled from audio files located on a PC. Some software shells supported only one of these methods. Over time, the software acquired additional capabilities, for example, copying any files, not just those supported by the player, which made it possible to use it as a storage device (the function was nicknamed Data Taxi). However, the fact that this operation required installation of drivers and software on the PC seriously reduced the usefulness of this function. As a rule, there was no talk at all about the high aesthetic qualities, impeccable work and good ergonomics of the shells. Users then were, for the most part, harsh and unspoiled people: they copied files to the player - and that’s fine.
Most manufacturers went through proprietary systems: iriver, Rio Audio, Creative, Cowon, Mpio, etc. Each of these manufacturers at one time had their own drivers and their own software, some more successful, some less successful. In any case, having changed the player to a device from another manufacturer, the user was forced to adapt to the new shell with its logic and features. Many manufacturers continue to equip their devices today with these programs as an alternative to MSC/UMS standards or MTP solutions.
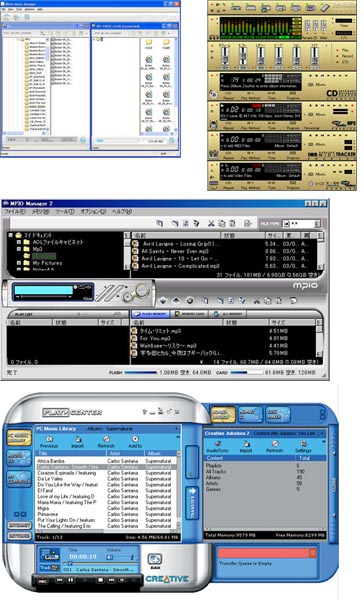
Proprietaryshell-managers: Iriver Music Manager, Cowon JetAudio, Mpio Manager, Creative Play Center
The zoo of all kinds of shells could not suit consumers (they could still put up with the existence of a bunch of motley drivers). It also did not suit manufacturers, especially small ones who did not have the resources to develop high-quality software. Therefore, in 1999 - early 2000s, the use of third-party shells gained some popularity.
Among them is the MusicMatch Jukebox program.

InterfaceMusicMatch Jukebox
Before the advent of iTunes for Windows PC, it was used here to work with the Apple iPod. It also worked with players from other manufacturers, such as RCA-Thomson.
Programs like MusicMatch Jukebox were the first seeds of standardization. They made it possible to use players from different manufacturers without installing additional software for each of them. The solution was not flawless, it was just a step from varied protocols and shells to standardized solutions. In this case, only the protocol control interface was standardized; installing separate drivers for each device was still necessary. The shells themselves were not part of the operating system; they had to be installed separately, from the Internet or from the accompanying CD. Their functionality, stability and convenience often also raised questions. Not all players were supported, which forced manufacturers to equip their devices with plugins for popular program managers.

Available for download on the websiteRCA-Lyra: primarily a plugin forMusicMatchJukebox and only then your own shellLyraDJ
Usually, over time, the program “grew fat”, became overgrown with unnecessary functions for the user, advertising, and required more and more resources.

Another popular shell in the past isRealJukebox
At the same time, competitive pressure was growing: in 2001, Windows Media Player became standard in Windows XP, and in 2003, iTunes for Windows appeared. Small Asian companies in 2002-2003 also found a good replacement for this software - the open MSC/UMS protocol. As a result, shells like MusicMatch Jukebox have fallen off the scene to give way to next-generation protocols. But their legacy was not in vain: the “one shell for different players” model was largely inherited by the Microsoft PlaysForSure system.
One feature of proprietary systems, however, has allowed them to survive longer than is reasonable in certain markets. Their closed nature created obstacles when using the player to freely transfer data from PC to PC, that is, according to the RIAA, when using it as a tool for digital piracy. In troubled markets like America's, companies unwilling to draw too much attention to themselves continued to pursue a proprietary approach even after the rise of generic solutions.

On the siteiriver non-proprietary firmware is still specially noted asUMS orMTP
Here you can remember, for example, iriver or Creative. iriver players were generally produced in two versions: for the US market - working through a proprietary protocol, for others - through open MSC/UMS. This “life after death” for closed protocols continued until the release of the MTP protocol in 2004, which, being relatively universal, also suited record companies.
Period 2002-2004 was a transition from the “dark ages” of closed systems to the relative openness of modern protocols. Today, pure proprietary protocols are completely out of use.
You've probably heard the phrase, "you need to use a VPN to protect your privacy." Now you're thinking, "Okay, but how does a VPN work?"
There are many articles on the Internet that suggest using a single protocol, but few have taken the time to explain some of the basic VPN technologies. In this article, I'll explain what VPN protocols there are, their differences, and what you should look for.
What is a VPN?
Before we look at specific VPN protocols, let's quickly recap what a VPN is.
Essentially, a VPN allows you to access the public internet using a private connection. When you click a link on the Internet, your request goes to the correct server, usually returning the correct content. Your data essentially flows seamlessly from A to B, and the website or service can see your IP address among other identifying data.
When you use a VPN, all your requests are first routed through a private server owned by the VPN provider. Your request goes from A to C via B. You can access all the data previously available to you (and in some cases, more). But the website or service only has the VPN provider's details: their IP address, etc.
There are many uses for a VPN, including protecting your data and identity, avoiding oppressive censorship, and encrypting your communications.
What are VPN protocols?
The VPN protocol determines exactly how your data is routed between your computer and the VPN server. The protocols have different specifications, offering benefits to users in a variety of circumstances. For example, some prioritize speed, while others focus on privacy and security.
Let's look at the most common VPN protocols.
1. OpenVPN
OpenVPN is an open source VPN protocol. This means that users can check the source code for vulnerabilities or use it in other projects. OpenVPN has become one of the most important VPN protocols. OpenVPN is open source and is one of the most secure protocols. OpenVPN allows users to protect their data using essentially unbreakable AES-256 key encryption (among others), with 2048-bit RSA authentication and 160-bit SHA1.

In addition to providing strong encryption, OpenVPN is also available for almost every platform: Windows, MacOS, Linux, Android, iOS, routers and more. Even Windows Phone and Blackberry can use it!
The OpenVPN protocol has been criticized in the past due to its slow speeds. However, recent implementations have seen some acceleration, and the focus on security and privacy is noteworthy.
2.L2TP/IPSec
Layer 2 Tunnel Protocol is a very popular VPN protocol. L2TP is the successor to the deprecated PPTP (see PPTP section below for more details) developed by Microsoft and L2F developed by Cisco. However, L2TP does not actually provide any encryption or privacy.

Accordingly, services using L2TP are often associated with the IPsec security protocol. Once implemented, L2TP/IPSec becomes one of the most secure VPN connections. It uses AES-256 bit encryption and has no known vulnerabilities (although IPSec was allegedly compromised by the NSA).
However, while L2TP/IPSec has no known vulnerabilities, it does have some minor disadvantages. For example, by default the protocol uses UDP on port 500. This makes it easier to detect and block traffic.
3.SSTP
The Secure Socket Tunneling Protocol is another popular VPN protocol. SSTP has one notable advantage: it has been fully integrated with every Microsoft operating system since Windows Vista SP1. This means you can use SSTP with Winlogon or, for added security, a smart chip. Additionally, many VPN providers have specific SSTP instructions built-in for Windows. These can be found on the VPN provider's website.

SSTP uses 2048-bit SSL/TLS certificates for authentication and 256-bit SSL keys for encryption. Overall, SSTP is quite secure.
SSTP is essentially a Microsoft proprietary protocol. This means that no one can fully inspect the underlying code. However, most of them still consider SSTP secure.
Finally, SSTP has native support for Windows, Linux, and BSD systems. Android, macOS and iOS support third-party clients.
4. IKEv2
Internet Key Exchange version 2 is another VPN protocol developed by Microsoft and Cisco. IKEv2 itself is a tunneling protocol that provides a secure key exchange session. Therefore (like its predecessor), IKEv2 is often paired with IPSec for encryption and authentication.
Although IKEv2 is not as popular as other VPN protocols, it has many mobile VPN solutions. This is due to the fact that it is able to reconnect during moments of temporary loss of Internet connection, as well as during a network switch (for example, from Wi-Fi to mobile data).

IKEv2 is a proprietary protocol with native support for Windows, iOS and Blackberry devices. Open source versions are available for Linux, and Android support is available through third-party applications.
Unfortunately, while the ikev2 protocol is great for mobile communications, there is strong evidence that the US NSA is actively exploiting its flaws to undermine IPSec traffic.
5.PPTP
Point-to-point tunneling protocol is one of the oldest VPN protocols. It is still used in some places, but most services have long since upgraded to faster and more secure protocols.
PPTP was introduced back in 1995. It was actually integrated with Windows 95, designed to work with dial-up connections. This was extremely helpful at the time.

But VPN technology has progressed and PPTP is no longer secure. Governments and criminals have long broken PPTP encryption, rendering any data sent using the protocol unsecured.
However, it is not completely dead yet.... You see, some people believe that PPTP gives better connection speeds precisely because of the lack of security features (compared to modern protocols). Thus, it is still used as users simply want to watch Netflix from another location.
Let's Summarize VPN Protocols
We've looked at five major VPN protocols. Let's quickly summarize their pros and cons.
OpenVPN: is open source, offers the strongest encryption suitable for all activities, has slightly slower connection times.
L2TP/IPSec: Widely used protocol, good speeds, but easily blocked due to dependency on a single port.
SSTP: good security, difficult to block and detect.
IKEv2: fast, mobile-friendly, with several open source implementations (potentially undermined by the NSA).
PPTP: fast, widely supported but full of security holes, only used for streaming and basic web browsing.
For complete security and peace of mind, choose a VPN provider that offers you a choice of protocols. Alternatively, you may want to use paid VPN solutions like ExpressVPN rather than a free service. When you pay for a VPN, you are purchasing a service. When you use a free VPN, you have no idea what they can do with your data.
What VPN protocol do you usually use? Does your VPN provider offer choice? Tell it in the comments!
Today I will talk about a wonderful broadcast protocol RTMFP. It implements many interesting approaches and there are a lot of prejudices regarding its capabilities. I want to stir up interest in this topic and dispel existing illusions. I haven't found anything better for live broadcasting, so I decided to write this post.Background
A long time ago in a galaxy far away...In 2004 there lived Amicima, Inc. in which the GPL protocol implementation was developed MFP - MFPNet. Then they released amiciPhone- one of Skype's competitors, but due to positioning problems things did not go very well. In 2007, they were acquired by Adobe because they needed a good real-time broadcast protocol.
What's wrong with RTMP?
RTMP is not a real-time broadcast protocol:- the problem of minimizing delays is not solved;
- broadcasting stops when the device address is changed;
- TCP significantly increases latency and bloats messages with unnecessary delivery checks;
- no window size control.
Preconceptions about RTMFP
This is a proprietary protocol
Adobe decided to publish it in the form RFC7016 in order to stir up public attention, but somehow it worked out. Oddly enough, this doesn't look like a crooked RTMP specification and looks more like MFP.The protocol itself is modular: certificate exchange, encryption, and stream synchronization are implemented as a separate profile. What happens in Flash stays in Flash. For developers of third-party solutions, such as Cumulus,Flash remained a black box; somehow quietly and imperceptibly came out in April 2014 Adobe's RTMFP Profile for Flash Communication.
This is UDP - which means there is no guarantee of delivery
Quite a few real-time protocols use UDP and add a network checksum and selective delivery checks to guarantee delivery. They check only what must come, and not everything in a row. For audio/video, controlling packet delivery doesn't make much more sense. The window size (MTU) is usually maximum and static, which increases the likelihood of an empty playback situation with subsequent reception of irrelevant data when a packet is lost.We don't need RTMFP - we have WebRTC
WebRTC this is not a protocol, it is a browser technology - an attempt to integrate SIP with an RTP stack into a browser. If you combine RTP, SRTP, SCTP, RTCP, ZRTP, RTSP, you get RTMFP. But in a number of cases, such connections have redundancy and problems with addressing that are not present in RTMFP.RTMFP has forwarding through NAT, window size control, metadata for streams with redundancy control on the application side, forwarding/redirecting sessions, and its own DHT.
How many RTP-like protocols do you need to encapsulate in order to implement all this?.. I think about 4-5 pieces.
The current implementation of broadcast protocols resembles the situation:
“There are 6 protocols, but they all have a fatal flaw, and we will develop another one...”
A year passes.
"There are 7 protocols, and they all have a fatal flaw..."
RTMFP is not an attempt to replace existing solutions. This is an attempt to generalize them, get rid of redundancy and make them accessible to users.
RTMFP and OSI model
So, let's look at what layers of the OSI model the RTMFP protocol covers.Physical and channel
There are no ephemeral energy fluctuations from fluttering butterflies, but we would like redundancy through data transfer in warp subspaces.Network and transport
These are IP and UDP multicast.
There is Path MTU discovery and Congestion Control, already in the box, for each specific stream. There is a data transmission mode with a selective delivery check frequency - we check it once every N packets. All packages are timestamped to measure delivery delay. Built-in ring hash addressing for DHT endpoints.Presentation layer
For Flash, this is, of course, AMF3 and encapsulated RTMP, but any other data can be transmitted.
Security in RTMFP
- Classic Diffie-Hellman key exchange with static and ephemeral keys.
- Cookies and certificates in sessions, with the ability to digitally sign packages. True, by default unsigned packages are considered valid
- AES128 is used for encryption, but any other block algorithm can be used.
- HMAC-SHA256 or network checksums.
Where's the killer feature?
I think everyone remembers the failure of the broadcast of the latest presentation of the new pop phone IPhone 6 Plus?So imagine that one client receives an incoming stream and broadcasts it to two more or more (if possible), and so on - as long as the maximum possible delay allows. At the same time, permutations and sorting occur in the client tree in real time in order to minimize delays and optimize the package window. As a result, you can achieve a multiple reduction in the outgoing traffic of the broadcast server.
And everyone will see him...
Use Cases
Broadcast content in real time
Actually, this is the purpose of the protocol itself, and it copes with this task very well.
It can be used not only for audio/video transmission, but also as the main transport in Flash games.CDN
This is P2P and to download a file you only need to know its name, hash and size.
You can implement an http2rtmfp gateway - the possibilities are quite interesting.Video conferencing and chats
In the post-Snowden era, RTMFP is an accessible and secure P2P transport. Also, the main advantage is the ability to continue broadcasting when the device’s network address is changed. WebRTC may fall off when changing cells in 3G/4G. The RTP stack is not well suited for broadcasting in such an environment.Real-time data transfer within private networks
The main advantage for this use case is the possibility of flexible routing policies, minimizing delays, optional packet delivery verification and built-in traffic prioritization tools. All this can be configured individually for each specific application.
What's the deal with existing RTMFP solutions?
In short, things are very bad. Today, the only open implementation is Cumulus. It develops very sluggishly. Based not on the RFC, but on the first reverses of the Cirrus 1 RTMFP, so compatibility with the current Cirrus 2 Flash Profile is rather questionable. It implements most of the utilities, including organizing redundancy in P2P and broadcasting between devices. There is FMS, but it works like FMS...I will be glad to receive constructive comments.
In the comments, please indicate analogues of RTMFP if you know them.
July 17, 2017 , BIS Journal No. 3(26)/2017
Comparison of secure access technologies and protocols
VPN is an integral part of all information security systems, including those that protect the information systems of financial organizations. This technology is the simplest, most understandable and affordable way to safely unite geographically distributed sites and reliably protect information when transmitted over public networks.There are many scenarios for using VPN: organizing interaction between remote offices, connecting remote employees or clients, connecting ATMs, accessing data centers in which the resources of the bank’s information systems are concentrated. In addition to the task of ensuring interaction, in some cases, VPN allows you to create a clear protection perimeter and ensure the availability of segments of the information system.
However, before you begin choosing a specific solution provider, it is necessary and important to understand what VPN technologies exist and what the differences are between them.
PROPRIETARY PROTOCOLS
All protocols for data transmission are divided into two categories.
The first category that will be discussed is proprietary (closed) protocols and technologies that are the intellectual property of individual companies. The advantages of this approach are that the technology can be relatively quickly modified to meet the requirements of the equipment manufacturer or the wishes of a specific customer. However, there are also a number of disadvantages.
Firstly, there is a high probability for the customer to become the object of research and technical improvements at his own expense. In order to reduce the risk of architectural errors, it is necessary to work out the new technology as fully as possible with the involvement of the widest possible range of experts. Unfortunately, the customer base of Russian vendors using proprietary protocols does not always allow this. By the way, foreign IT market leaders do not follow the path of creating proprietary protocols. They develop the functionality of generally accepted protocols, open access to their technology and make it public, available to other manufacturers.
Secondly, a significant disadvantage is that non-standard product design and undocumented device behavior can make the customer dependent on the product supplier. If the quality of the service or services no longer suits the customer, switching from a proprietary protocol to another can be extremely costly, or even impossible without a complete overhaul of the security system. In the best case, the customer can count on using used hardware platforms on which new software can be installed. Specialists from S-Terra CSP already had experience installing their VPN gateway on the platforms of Stonesoft (which, although it used standard protocols, is known to have ceased active activity in the network security market in Russia).
Thirdly, any non-standard design creates problems when troubleshooting or malfunctioning devices. It is necessary to have on staff people who know the behavior of both standard equipment and the specific operation of technologies from a particular manufacturer.
And fourthly, you need to take into account the fact that a proprietary protocol has minimal chances of achieving compatibility with other manufacturers.
PUBLIC PROTOCOLS
The second category is public (or standard) protocols, which can be used in equipment manufactured by various vendors. A description of these technologies is given in special documents (Request for Comments, RFC) of the Internet Engineering Task Force (IETF). They are created and supplemented by the best industry experts. For VPN, the most commonly used public protocols are IPsec and SSL in various variations.
SSL (TLS)
This family of protocols is designed to provide remote client access and is targeted at specific user applications. There are several options for using SSL (TLS):
Clientless mode. This mode uses one-way authentication from the server to the client side. In this case, the user does not need to install specialized client software to protect traffic; it is enough to have only a crypto provider on the workstation. Working in this mode is only possible with Web applications, and in Russian realities there is a connection to the not very popular Internet Explorer browser. This mode of operation is suitable, for example, for a limited list of scenarios for secure access to a web portal.
Client mode. If you need to provide access to any other application, a special SSL (TLS) client is used. In this mode, it is possible to use two-way authentication.
One of the main advantages of the protocol is the absence or minimal need for personal client configuration. However, if new software is installed on the workstation or a new service appears that requires access, the user will need to add these parameters to the client settings.
You also need to take into account the fact that standard SSL operates at the application level and cannot protect traffic from network equipment or network segments. The DTLS protocol can solve this problem, but it also has a client-server model and is not widely used among Russian manufacturers.
IPsec operates at a lower layer of the OSI model and does not require application support to operate. It is perfect for creating secure connections both between branches in a geographically distributed network, and for organizing secure remote access.
Due to the protocol operating at the network level, VPN operation does not require changes to the software at the workplace. All user applications work “transparently” and do not know about the existence of the VPN. The protocol always provides two-way authentication.
When implementing remote access, personalized client configuration is required for each specific workstation. At the same time, the client protects all network interactions between the workstation and the remote network. Consequently, the need to have means of protection against unauthorized access to workstations at users' workplaces is more urgent than in the case of SSL.
IPsec is the most well-known protocol for building VPNs and continues to evolve. The second version of the IKE key distribution protocol has appeared; the protocol stack is part of the IPv6 standard.
In addition to the above, the standard protocols IPsec and SSL (TLS) have certain advantages in Russian realities. We are talking about the activities of the technical committee for standardization “Cryptographic information protection” (TC 26) in the field of developing recommendations for the use of uniform replacement nodes and elliptic curve parameters in Russian GOST standards for cryptography, as well as their use in data transfer protocols. This activity has already borne fruit - a number of Russian manufacturers, including the S-Terra SSP company, have ensured the compatibility of their certified solutions when using the IPsec protocol. Of course, if proprietary protocols had been used, such results would not have been achieved. Although such processes do not happen quickly, customers have the prospect of fulfilling their cherished dream - the emergence of technical compatibility of various certified VPN solutions with each other.
The use of standard protocols in different areas (Syslog, SNMP, Netflow, etc.) allows you to combine products into a single system. For example, this practice is generally accepted when solving problems of monitoring and building SIEM systems.
WE Draw CONCLUSIONS
When choosing a standard protocol, the customer must determine the desired use case. If it is enough for him to protect only individual services and ease of setup is important - SSL (TLS), if full network connectivity between objects is necessary - his choice is IPSec.
At the same time, it must be remembered that in addition to the data transfer protocol, each solution has a large number of different technologies and features. Therefore, it is worth evaluating and comparing products as a whole, depending on the task at hand.
Not enough). The copyright holder of proprietary software retains a monopoly on its use, copying and modification, in whole or in significant respects. Typically, proprietary software refers to any non-free software, including semi-free.
The concept in question is not directly related to the concept commercial software .
Etymology
FSF
The term "proprietary software" is used by the FSF (Free Software Foundation) to define software that is not considered free software by the Foundation. .
Semi-free software
Free software, which allows virtually unlimited use, distribution and modification (including distribution of modified versions) of software for non-commercial purposes, was previously called semi-free by the Free Software Foundation. Like Debian, the Free Software Foundation considered these conditions unacceptable for free software, but distinguished semi-free software from proprietary software. “Proprietary software” and “semi-free software” were collectively called “proprietary software.” The FSF later abandoned the concept of "semi-free software", and began using the term "proprietary software" for all proprietary software.
Restrictions
Prevention of use, copying or modification may be achieved by legal and/or technical means.
Technical measures include releasing only machine-readable binaries, limiting access to human-readable source code (closed source), and making it difficult to use hand-made copies. Access to proprietary code is usually limited to employees of the development company, but more flexible access restrictions may apply in which the sharing of source code is permitted to company partners, technical auditors, or others in accordance with company policy.
Legal means may include trade secrets, copyright and patents.
Legal protection
Legal protection of computer programs is possible under two different legal regimes - the regime applied to literary works and the regime applied to patents. In the first case, the program is identified (and protected) by the text of the code, in the second - by the patentability criteria used for inventions (that is, it is necessary to prove “innovation”, “originality” and “non-obviousness”, as well as the ability to solve an existing technical problem and commercial suitability ).
Legal protection of computer programs is based on the provisions of a number of international agreements and conventions. However, almost all of them to one degree or another (such as the Paris, Berne, Rome Conventions and the Washington Treaty) are incorporated into the text of the TRIPS Agreement, administered by the World Trade Organization. The TRIPS Agreement provides that computer programs are protected "similarly to literary works under the Berne Convention (1971)." However, in practice, the second mode of protection of proprietary digital content in the form of a patent is increasingly being used (Article 27 of TRIPS). For example, in the US, the first US software patent was issued in the 50s, Patent No. 3,380,029 dated. issued to Martin A. Goetz. However, a full-fledged legal doctrine of patenting computer programs in the United States was formed only in the 1980s as a result of a number of judicial precedents (Gottschallk v. Benson; Diamond v. Diehr.), which developed special criteria applicable to patenting computer programs. Until this time, it is impossible to talk about patenting computer programs in the United States as a well-established procedure. One of the last patents for a computer program was a patent issued on January 6th. No. US 9,230,358 B2, which protects a method, system and computer program for rendering widgets. In the EU, patenting of computer programs is based on the EPC provision, which has been clarified by a number of decisions of the European Patent Office. In case No. T258/03 (Hitachi / Auction method) dated April 21, 2004, the Board of Appeal of the European Patent Office indicated that Art. 52 (1) and 52 (2) EPC does not prohibit the patenting of computer programs, but not every “technical solution” can be patented. According to representatives of the patent office, the use of “technical means” to solve the problem is quite understandable, but it presupposes the need to supplement the “technical solution” with an “innovative” one.
Typical Limitations of Proprietary Software
There are a large number of different business models, and proprietary software companies write their own licensing agreements to accommodate them. The most common limitations of proprietary software are listed below.
Restriction on commercial use
There are a huge number of software products that allow free use for non-commercial purposes for individuals, medical and educational institutions, non-profit organizations, etc., but they require payment if the software product is used for profit. Such software is very popular and widely used, and due to its free nature, it has good technical support from specialists who do not have the need for additional training costs.
Restriction on distribution
This type of restriction usually accompanies large software projects, when the copyright holder requires payment for each copy of the program. Typically, such a restriction is applied to software products aimed at a narrow “professional” segment of the market or for software required by a large number of users. An example would be the Adobe CS6 software package or the Windows 8 operating system.
Restriction on study, modification, etc.
This type of restriction is used only in closed source software packages and may prohibit or restrict any modification of the program code, disassembly, and decompilation.
Proprietary by default
For legal and technical reasons, the software is usually proprietary by default.
Software in compiled languages is used in a form not intended for editing, that is, without source code. The author may not distribute the source texts out of habit, or may not consider them of sufficient quality to be worth showing.
Due to the variety of licenses, it can be difficult for an author to choose the best one.
Among free software advocates, there are differing opinions about the importance of user freedoms in relation to software that runs only on a remote system (server software, which was not subject to the copyleft terms of the GNU GPL, which gave rise to the Affero GPL), or as if "on the Internet" ", but in fact each time it is downloaded for execution on the user's computer (for example, scripts from websites, sometimes occupying hundreds of kilobytes with unreadably shortened function names), or algorithms implemented in hardware (which reduces the share of conventional proprietary BY, but does not make him freer user). See GNU AGPL, open hardware, GNUzilla (a web browser with an add-on that blocks the execution of non-trivial non-free JavaScript programs).
Notes
- Proprietary Yandex dictionaries
- Since commercial software can be free: Some Confusing or Loaded Words and Phrases that are Worth Avoiding(English) . Free Software Foundation. Retrieved December 1, 2008. Archived February 3, 2012.
