Checking anonymity and what the provider knows. Checking the VPN connection configuration
It's very easy to hide or change your IP address. All you need is a VPN (virtual private network).
When you connect to a VPN, your IP address is replaced with a different one, and everything looks as if you are in the other place. When you use a VPN, your internet traffic is routed through an encrypted tunnel so that no one, including your ISP, can see what you do online.
When connected to a VPN, it will appear as if you are in the same location as the server. For example, if you are in the US and connect to a VPN server in the UK, you are virtually in the UK.
What is an IP address?
An Internet Protocol address (IP address) is a unique number assigned to all devices (such as a computer, tablet, or phone) that connect to the Internet.
IPv4 and IPv6 addresses
There are currently two versions of the Internet Protocol in use: version 4 (IPv4) and version 6 (IPv6), and they have two main functions: identification and address assignment.
The sixth version of the Internet Protocol (IPv6) was created in 1995 as a preventative measure to ensure that there would be enough addresses available for the foreseeable future (IPv6 uses 128-bit IP addresses, resulting in 3.4 x 1038 addresses, whereas the IPv4 protocol version uses 32-bit IP addresses and there are about 4 billion addresses in total).
You will not be able to access the Internet without public IP address
To use the Internet, all connected devices must have a public IP address, which allows two devices—the sender and the recipient of Internet communications—to find each other and exchange information.
This is similar to a real address system. For example, if you wanted to subscribe to a magazine, the magazine distributor (the sender) would need your address in order to send you (the recipient) your copies. Without your address, distributors wouldn't know where to send the magazine.
The same goes for the Internet. Without an IP address, two devices will not be able to find each other and exchange information.
What is a private IP address?
Private networks use private IP addresses to identify and exchange information between computers and devices, such as a printer, that are not directly connected to the Internet.

All computers and devices on your home network have a unique private IP address to communicate with each other, but outside the local network they are not visible and cannot be connected to.
The most common reason why a user wants to access the Internet anonymously is because they are banned somewhere. Each computer has a unique impression, consisting of such characteristics as: IP address, country, city, operating system, browser name and version, screen resolution, etc. When you visit the site, all this information is collected and stored. The next time you visit, the computer is also identified, and the system determines whether you are banned or not.
How anonymous is your online experience?
Good people, as always, came up with everything before us :) There is a special free service that will help you determine your IP and check the degree of visibility on the Internet. So, go to the website https://whoer.net/ru and look:
To increase anonymity you need to use a proxy server. I immediately logged in via VPN to show that my country was defined as Germany, but the city and region were not defined at all. Below you also find information about whether Javascript and Java are working for you.
Interestingly, the service shows whether the IP address is blacklisted. For example, mail sent from a blacklisted IP address may end up in the Spam folder at gmail.com, etc. For a long time I could not understand why not a single letter of mine reached the recipients if I sent it from an email program, and everything worked fine if I sent mail from the browser. It turned out that my IP was blacklisted as a spammer. This situation can easily happen if you have .
To get more information, you need to go to the "Advanced Version" tab. There is more complete technical information here, for example, whether Flash works for you, what add-ons are installed in the browser, screen resolution and other details. Who knows what to look for, will find it. The less truth you find, the more anonymous your computer is. In general, to determine the basic parameters of anonymity, the first page of information will be enough for most.
There was even such a trick before, I don’t know if it exists now. In general, the user ends up on the site of a supposedly cool antivirus or firewall, and they write to him that he has such and such a browser installed, he lives in such and such a city, la-la-la poplars... The emphasis is on the fact that all information is easy to find out, because The computer is, like, not protected. And, as you probably already guessed, “good” protection is offered for a “symbolic” fee. Particular cynics sold them their virus :) This is a pure scam, but the fact that some information about a computer is available on the Internet is normal.
With similar functionality, which I recently wrote.
The main idea is to determine whether the user is hiding while surfing the Internet or not, and, if possible, find out his real IP address. There are several interesting features that I have never seen anywhere (two-way ping, matching DNS leak/ISP pairs).
I wanted to have a kind of checklist at hand that would answer whether you are “scorched” or not? At the moment, the list consists of 12 verification methods, which will be discussed below, including how not to fall for them, but first, the simplest ones in order.
HTTP proxy headers
Some proxies append their headers to the request that the user's browser initiates. Often this is the user's real IP address.Make sure that the proxy server, if it writes anything in the headers listed below, is at least not your address:
HTTP_VIA, HTTP_X_FORWARDED_FOR, HTTP_FORWARDED_FOR, HTTP_X_FORWARDED, HTTP_FORWARDED, HTTP_CLIENT_IP, HTTP_FORWARDED_FOR_IP, VIA, X_FORWARDED_FOR, FORWARDED_FOR, X_FORWARDED, FORWARDED, CLIENT_IP, FORWARDED_FOR_IP, HTTP_PROXY _CONNECTION
Open HTTP proxy ports
The IP address from which the request to our page came can say a lot. For example, can you see what ports are open on that side?The most interesting ports are 3128, 1080, 8123. If you do not use them, then you can completely avoid unfounded suspicions about using 3proxy, SOCKS 5 or Polipo.
Open web proxy ports
As with HTTP, a web proxy can be set to any port, but we wanted the test to work very quickly, so we limited ourselves to the reverse connection to ports 80 and 8080.Is the web page being given away? Great! At the moment we can detect PHProxy, CGIProxy, Cohula and Glype.
Suspicious host name
Having an IP address, you can try to resolve the client’s hostname. Stop words that may hint at a tunnel: vpn, hide, hidden, proxy.You shouldn't link domain names to your personal VPN, and if you do, you should avoid "speaking" names.
Difference in time zones (browser and IP)
Based on GeoIP data, you can find out the country by the user’s IP, and therefore his time zone. Next, you can calculate the time difference between the browser and the time corresponding to the time zone of the VPN server.There is a difference? This means the user is probably hiding.
For Russia there is no exact base of latitude and longtitude for regions, and since there are many time zones, in the end result we do not take these addresses into account. With European countries it’s the other way around; they are very good at firing.
When switching to a VPN, you need to remember to change the system time, change the time in the browser, or work with Russian proxies.
IP affiliation with the Tor network
If your IP address is a Tor node from the list check.torproject.org/cgi-bin/TorBulkExitList.py, congratulations, you're burned.Nothing criminal, but the fact that you are hiding is not very encouraging.
Browser Turbo mode
By collecting the IP address ranges of Google, Yandex and Opera, and comparing them with the user address, we can assume the use of traffic compression services in the browsers of the corresponding companies.As a rule, such services also leak your real address in the headers. As a means of anonymization, you should not rely on traffic compression.
Web proxy definition (JS method)
By comparing window.location.hostname with the host of the requested page, you can determine whether a web proxy is being used.Web proxies are not reliable in principle, so it is better to bypass such anonymization methods completely.
IP leak via Flash
Adobe Flash works very well past custom proxies. By initiating a connection to our server, you can find out the user’s IP.By running a special daemon that logs all incoming connections with tag keys, you can learn a lot. The best way to avoid revealing your address is to not use Adobe Flash at all, or disable it in your browser settings.
Tunnel detection (two-way ping)
By running a ping to the client IP from our server, you can find out the approximate length of the route. The same can be done from the browser side, XMLHTTPRequest pulls an empty page of our nginx. The resulting loop difference of more than 30 ms can be interpreted as a tunnel.Of course, the routes there and back may differ, or the web server may be a little slow, but overall the accuracy is quite good.
The only way to protect yourself is to deny ICMP traffic to your VPN server.
DNS leak
Finding out which DNS the user uses is not a problem; we wrote our own DNS server, which records all calls to our uniquely generated subdomains.The next step was to collect statistics on several million users, who uses what DNS. We linked to providers, discarded public DNS and received a list of DNS/ISP pairs.
Now it’s not at all difficult to find out if a user introduces himself as a subscriber of one network, but uses DNS from a completely different one.
The problem is partially solved by using public DNS services, if this can be called a solution.
Leak via VKontakte
This is not a leak of an IP address, but we still believe that by giving away the names of authorized users to everyone left and right, VK is leaking private data that undermines the anonymity of surfing.More details can be found in the documentation here
It happens in life that you need 100% anonymity when using the Internet through a browser (I’ll do without examples, otherwise tough guys will come to the comments again and accuse me of incitement and threaten me with department “K”). How to make sure that sites on the Internet (for example Google) cannot identify you and record information about any actions in your file?
It happens that you turn on a VPN with “incognito” mode, you don’t log in anywhere, and AdSense suddenly scares you with painfully familiar ads. How does he determine who is who?
To answer this question, let's conduct an experiment. Let's open tabs in four browsers:
- Tor Browser 6.0.2 (based on Mozilla Firefox 45.2.0);
- Safari 9.0 (incognito mode);
- Google Chrome 52.0.2743.82 (incognito mode);
- Mozilla Firefox 46.0.01 (incognito mode).
And let's see what data they can collect about a person. What do we tell the site about ourselves by typing the URL in the address bar?
We provide unique image rendering options (Canvas Fingerprinting)


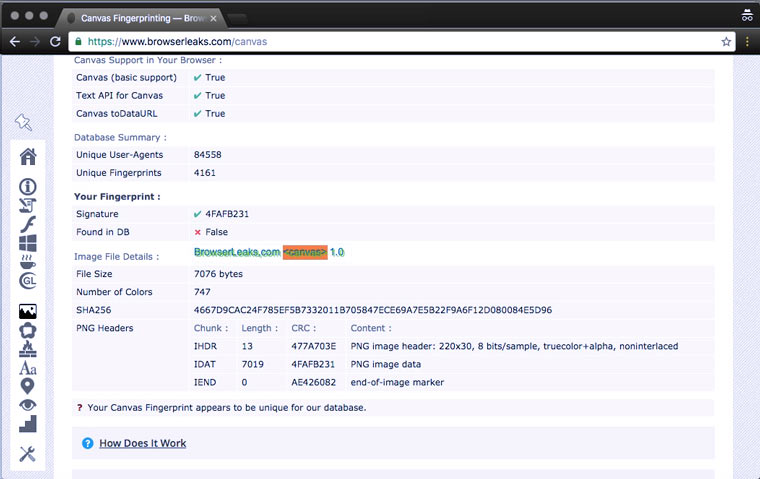

Canvas Fingerprinting is a user identification technology developed about 4 years ago at AddThis. The principle of its operation is based on the fact that when, when loading a page, a picture is drawn (rendered) (usually a single-color block in the background color with invisible text), the browser collects a bunch of information about the system for this: what hardware and graphics drivers are available, GPU version , OS settings, font information, anti-aliasing mechanisms and many other little things.
Together, this huge variety of details forms a unique characteristic that can distinguish a user's computer/browser combination from all others in the world. For each, it is written as a string similar to DA85E084. There are matches (according to Panopticlick, the average chance of finding a double is 1 in), but in this case, you can supplement them with other opportunities for identification (more on them below).
Tor asks permission to receive Canvas Fingerprinting, and if you are careful and do not give consent, you can keep this information to yourself. But all other browsers surrender their owner without a single peep.
You can read more about this identification method in Wikipedia.
We break through the database of advertising preferences




Many visited sites are now equipped with scripts for determining Canvas Fingerprint. Having received this unique value, one site can ask another for information about the person. For example, linked accounts, friends, IP addresses used and information about advertising preferences. Use the link below to check which systems have your consumer interests linked to Canvas Fingerprinting.
Tor again asked for the same permission as in the first point and, due to my refusal, nothing was found. Safari found me in 3 databases, Chrome in 13, and Firefox in 4. If you exit incognito mode, then in the latter the number of databases increases to 25, since most of them use good old cookies for identification.
We share the IP address and telecom operator


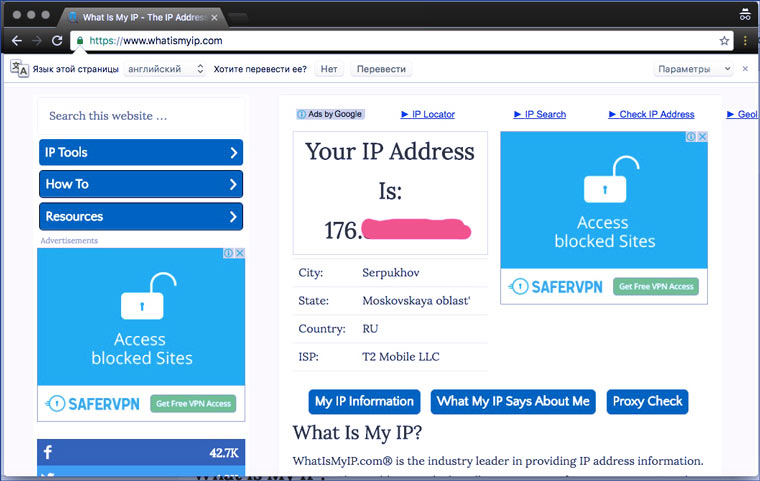

In Tor, you can change your “host country” using the New Identity button. And “incognito” modes do not hide your IP address (for this you must additionally use a proxy or VPN), but share your approximate location and information about your Internet provider with the site owners.
Revealing your city and the time in it (with geolocation services enabled)




On yandex.ru in Tor, without any location permissions, it showed where I was approximately and what time it was. It's the same with other browsers.
Send us your exact coordinates




Tor didn’t even ask permission to determine the coordinates and simply returned zeros. Safari, Chrome and Firefox asked for the standard resolution (as in normal mode) and did not bother to remind me that I was encrypted and should not reveal such data.
Revealing your city and the time in it (with geolocation services disabled)




Then I turned off location services on the Mac and went back to yandex.ru. Tor made the site think that I was in Romania, but left the time in Moscow (due to the mismatch of IP and time zone, it will be possible to ban VPN providers at once in the event of a ban). In other browsers everything remains the same.


The fact is that Yandex does not need GPS (or WPS data from the device) to determine location. After all, he has a “Locator”! Logged into the network via Wi-Fi? The access point is already in the database (see article). Did you give yourself internet from your phone? The cell tower will be rented.
We provide information about language settings




Another sure sign of a VPN lover is that the language does not match the country whose IP he is using. Tor let me down - its language is always English (but it can be changed, but I thought it should change automatically depending on the country). The rest of the settings are the same as in normal mode.
We tell you everything about your browser and system




Operating system, connection speed, monitor color characteristics, support for different technologies, browser window width, Flash version - a bunch of little things that complement the unique characteristics of the user. Tor manipulates some of this data (Windows 7 example), but other browsers are completely honest.
A person can change the IP, turn on “incognito”, and the script to raise prices will quickly calculate: “Who is this guy who came to us with a slow Internet, an old version of Flash and Windows XP for the second time, but now decided to pretend to be a resident of the Seychelles? We’re increasing it by 20%!”
We share a list of installed plugins
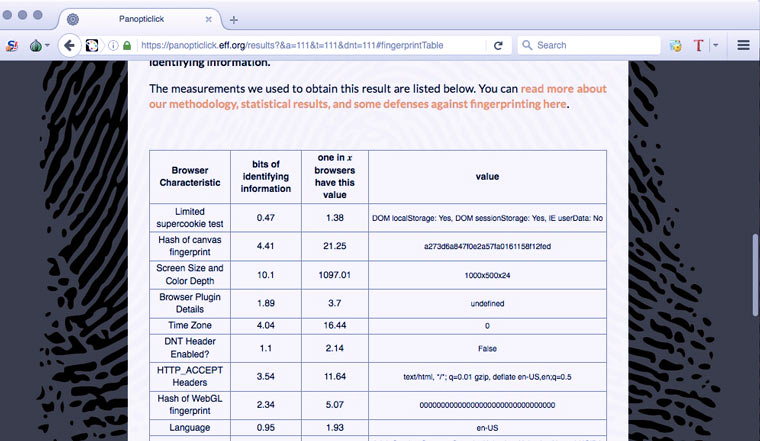



Another characteristic that adds uniqueness to a person is the list of plugins (with version information) installed in his browser. Tor hides them. Other browsers do not.
As you can see, Tor Browser provides good anonymity. But historical facts suggest that if a person does something really serious using the onion network, then he will still be sometimes they find. Everyone probably remembers the revealing story with the founder of Silk Road (a drug store) Ross Ulbricht.
And “incognito” modes are only needed to surf on someone else’s computer and not leave traces. In addition, you can block JavaScript, this will reduce the number of possible identification methods, but many sites will become unusable.
Open the list of fonts installed on the system (=> programs)

In addition to the experiment, I would like to talk about another interesting feature of modern browsers. Any site can get a list of fonts installed on the system. Many applications have their own unique fonts, and by using them you can determine a person’s occupation. And based on this, show him advertisements. In Tor and incognito mode this does not work (or the list is too short).
All this is the tip of the iceberg
To protect against the above identification methods, there are special plugins for different browsers. But you shouldn't waste effort installing them. Since they cannot protect against the collection of all possible information.
After all, in the article I showed the simplest and most understandable examples of how browsers collect information about us. But there could be much more of them: flash cookies, Silverlight cookies, time lag behind the standard time (many have at least 0.2-0.8 seconds) - many little things that would be superfluous. After all, the reader already understands that by opening a browser, he communicates a huge amount of information about himself to the world and demonstrates a set of unique characteristics that distinguishes his computer from all others.
What is the threat of all this information gathering?
You need to collect information about the majority of people on the planet for only one purpose - to increase the click-through rate of advertisements in order to earn more money from it. In principle, this is only beneficial - it is easier to find some goods or services.
More advanced identification methods are useful for stores to collect information about customers. So that a person cannot access the site under a different IP/disabling cookies and remain unrecognized. Language, time, rare font/plugin, monitor characteristics, a typical error in the search query you came from - and that’s it! Take off your skates, we recognize you. There is no doubt, this is the same person who placed order #2389 a year ago. With this data, automated marketing systems can sell him more.
Or, naturally, all this can be used by the intelligence services. But who knows how everything works there.
With similar functionality, which I recently wrote.
The main idea is to determine whether the user is hiding while surfing the Internet or not, and, if possible, find out his real IP address. There are several interesting features that I have never seen anywhere (two-way ping, matching DNS leak/ISP pairs).
I wanted to have a kind of checklist at hand that would answer whether you are “scorched” or not? At the moment, the list consists of 12 verification methods, which will be discussed below, including how not to fall for them, but first, the simplest ones in order.
HTTP proxy headers
Some proxies append their headers to the request that the user's browser initiates. Often this is the user's real IP address.Make sure that the proxy server, if it writes anything in the headers listed below, is at least not your address:
HTTP_VIA, HTTP_X_FORWARDED_FOR, HTTP_FORWARDED_FOR, HTTP_X_FORWARDED, HTTP_FORWARDED, HTTP_CLIENT_IP, HTTP_FORWARDED_FOR_IP, VIA, X_FORWARDED_FOR, FORWARDED_FOR, X_FORWARDED, FORWARDED, CLIENT_IP, FORWARDED_FOR_IP, HTTP_PROXY _CONNECTION
Open HTTP proxy ports
The IP address from which the request to our page came can say a lot. For example, can you see what ports are open on that side?The most interesting ports are 3128, 1080, 8123. If you do not use them, then you can completely avoid unfounded suspicions about using 3proxy, SOCKS 5 or Polipo.
Open web proxy ports
As with HTTP, a web proxy can be set to any port, but we wanted the test to work very quickly, so we limited ourselves to the reverse connection to ports 80 and 8080.Is the web page being given away? Great! At the moment we can detect PHProxy, CGIProxy, Cohula and Glype.
Suspicious host name
Having an IP address, you can try to resolve the client’s hostname. Stop words that may hint at a tunnel: vpn, hide, hidden, proxy.You shouldn't link domain names to your personal VPN, and if you do, you should avoid "speaking" names.
Difference in time zones (browser and IP)
Based on GeoIP data, you can find out the country by the user’s IP, and therefore his time zone. Next, you can calculate the time difference between the browser and the time corresponding to the time zone of the VPN server.There is a difference? This means the user is probably hiding.
For Russia there is no exact base of latitude and longtitude for regions, and since there are many time zones, in the end result we do not take these addresses into account. With European countries it’s the other way around; they are very good at firing.
When switching to a VPN, you need to remember to change the system time, change the time in the browser, or work with Russian proxies.
IP affiliation with the Tor network
If your IP address is a Tor node from the list check.torproject.org/cgi-bin/TorBulkExitList.py, congratulations, you're burned.Nothing criminal, but the fact that you are hiding is not very encouraging.
Browser Turbo mode
By collecting the IP address ranges of Google, Yandex and Opera, and comparing them with the user address, we can assume the use of traffic compression services in the browsers of the corresponding companies.As a rule, such services also leak your real address in the headers. As a means of anonymization, you should not rely on traffic compression.
Web proxy definition (JS method)
By comparing window.location.hostname with the host of the requested page, you can determine whether a web proxy is being used.Web proxies are not reliable in principle, so it is better to bypass such anonymization methods completely.
IP leak via Flash
Adobe Flash works very well past custom proxies. By initiating a connection to our server, you can find out the user’s IP.By running a special daemon that logs all incoming connections with tag keys, you can learn a lot. The best way to avoid revealing your address is to not use Adobe Flash at all, or disable it in your browser settings.
Tunnel detection (two-way ping)
By running a ping to the client IP from our server, you can find out the approximate length of the route. The same can be done from the browser side, XMLHTTPRequest pulls an empty page of our nginx. The resulting loop difference of more than 30 ms can be interpreted as a tunnel.Of course, the routes there and back may differ, or the web server may be a little slow, but overall the accuracy is quite good.
The only way to protect yourself is to deny ICMP traffic to your VPN server.
DNS leak
Finding out which DNS the user uses is not a problem; we wrote our own DNS server, which records all calls to our uniquely generated subdomains.The next step was to collect statistics on several million users, who uses what DNS. We linked to providers, discarded public DNS and received a list of DNS/ISP pairs.
Now it’s not at all difficult to find out if a user introduces himself as a subscriber of one network, but uses DNS from a completely different one.
The problem is partially solved by using public DNS services, if this can be called a solution.
Leak via VKontakte
This is not a leak of an IP address, but we still believe that by giving away the names of authorized users to everyone left and right, VK is leaking private data that undermines the anonymity of surfing.More details can be found in the documentation here
