Checking anonymity and what the provider knows. Checking the VPN connection configuration
Your IP
144.76.78.3
Browser used
In the services presented here you can check for proxy anonymity, which your browser is set to. These addresses are dynamically created pages that will show all or almost all (the most essential) information about you and your computer. The information presented on these pages can be obtained by anyone, including web server administrators, when you download (something), view pages - therefore we strongly recommend that you familiarize yourself with the section of the site
What can these services find out about you on the Internet?
leader.ru/secure/who.php- this address is for obtaining detailed information about your computer. Calculates not only the IP address, but also about your ISP.
ipid.shat.net- here contains basic information about you: identified IP address, browser, its version, operating system, etc.
www.samair.ru/proxy/proxychecker/- If you use a proxy server, check it for anonymity here.
www.all-nettools.com/toolbox,net- this proxy checking service is intended for beginners. Here you can find out information about your IP address.
If you have Java support enabled
Based on these addresses, your IP is calculated based on the included Java support.
If you have Java enabled, it will show your real IP.
Still"sProxy Checker Center- contains a set of proxy server tests for anonymity, including Java check
Environment Variables
Some sites have the ability to provide a report of the information that your computer transmits about itself to the Internet. Description of variables can be found here shadowsecurity.net.ua/r/checking3.shtml
As you understand, you can learn a lot about you from just your IP address.
What can an IP address tell you?
Use your IP address (for example):
www.all-nettools.com/toolbox
Enter the desired IP in the (SmartWhois) field and click the (Go) button
At a minimum, you will receive:
The maximum you can find out is:
With similar functionality, which I recently wrote.
The main idea is to determine whether the user is hiding while surfing the Internet or not, and, if possible, find out his real IP address. There are several interesting features that I have never seen anywhere (two-way ping, matching DNS leak/ISP pairs).
I wanted to have a kind of checklist at hand that would answer whether you are “scorched” or not? At the moment, the list consists of 12 verification methods, which will be discussed below, including how not to fall for them, but first, the simplest ones in order.
HTTP proxy headers
Some proxies append their headers to the request that the user's browser initiates. Often this is the user's real IP address.Make sure that the proxy server, if it writes anything in the headers listed below, is at least not your address:
HTTP_VIA, HTTP_X_FORWARDED_FOR, HTTP_FORWARDED_FOR, HTTP_X_FORWARDED, HTTP_FORWARDED, HTTP_CLIENT_IP, HTTP_FORWARDED_FOR_IP, VIA, X_FORWARDED_FOR, FORWARDED_FOR, X_FORWARDED, FORWARDED, CLIENT_IP, FORWARDED_FOR_IP, HTTP_PROXY _CONNECTION
Open HTTP proxy ports
The IP address from which the request to our page came can say a lot. For example, can you see what ports are open on that side?The most interesting ports are 3128, 1080, 8123. If you do not use them, then you can completely avoid unfounded suspicions about using 3proxy, SOCKS 5 or Polipo.
Open web proxy ports
As with HTTP, a web proxy can be set to any port, but we wanted the test to work very quickly, so we limited ourselves to the reverse connection to ports 80 and 8080.Is the web page being given away? Great! At the moment we can detect PHProxy, CGIProxy, Cohula and Glype.
Suspicious host name
Having an IP address, you can try to resolve the client’s hostname. Stop words that may hint at a tunnel: vpn, hide, hidden, proxy.You shouldn't link domain names to your personal VPN, and if you do, you should avoid "speaking" names.
Difference in time zones (browser and IP)
Based on GeoIP data, you can find out the country by the user’s IP, and therefore his time zone. Next, you can calculate the time difference between the browser and the time corresponding to the time zone of the VPN server.There is a difference? This means the user is probably hiding.
For Russia there is no exact base of latitude and longtitude for regions, and since there are many time zones, in the end result we do not take these addresses into account. With European countries it’s the other way around; they are very good at firing.
When switching to a VPN, you need to remember to change the system time, change the time in the browser, or work with Russian proxies.
IP affiliation with the Tor network
If your IP address is a Tor node from the list check.torproject.org/cgi-bin/TorBulkExitList.py, congratulations, you're burned.Nothing criminal, but the fact that you are hiding is not very encouraging.
Browser Turbo mode
By collecting the IP address ranges of Google, Yandex and Opera, and comparing them with the user address, we can assume the use of traffic compression services in the browsers of the corresponding companies.As a rule, such services also leak your real address in the headers. As a means of anonymization, you should not rely on traffic compression.
Web proxy definition (JS method)
By comparing window.location.hostname with the host of the requested page, you can determine whether a web proxy is being used.Web proxies are not reliable in principle, so it is better to bypass such anonymization methods completely.
IP leak via Flash
Adobe Flash works very well past custom proxies. By initiating a connection to our server, you can find out the user’s IP.By running a special daemon that logs all incoming connections with tag keys, you can learn a lot. The best way to avoid revealing your address is to not use Adobe Flash at all, or disable it in your browser settings.
Tunnel detection (two-way ping)
By running a ping to the client IP from our server, you can find out the approximate length of the route. The same can be done from the browser side, XMLHTTPRequest pulls an empty page of our nginx. The resulting loop difference of more than 30 ms can be interpreted as a tunnel.Of course, the routes there and back may differ, or the web server may be a little slow, but overall the accuracy is quite good.
The only way to protect yourself is to deny ICMP traffic to your VPN server.
DNS leak
Finding out which DNS the user uses is not a problem; we wrote our own DNS server, which records all calls to our uniquely generated subdomains.The next step was to collect statistics on several million users, who uses what DNS. We linked to providers, discarded public DNS and received a list of DNS/ISP pairs.
Now it’s not at all difficult to find out if a user introduces himself as a subscriber of one network, but uses DNS from a completely different one.
The problem is partially solved by using public DNS services, if this can be called a solution.
Leak via VKontakte
This is not a leak of an IP address, but we still believe that by giving away the names of authorized users to everyone left and right, VK is leaking private data that undermines the anonymity of surfing.More details can be found in the documentation here
Readers of Complitra ru are already familiar from our articles with various VPN services, their purpose and some of the nuances that are now so necessary for safe and somewhat free use of the Internet - without any restrictions or censorship of the web.
Today we will talk about the fact that not all providers (vpn providers) can provide (or ensure) a stable and high level of unconditional security on the Internet.
Let’s consider the most important aspects so necessary for a respectable user: let’s learn how to check your VPN service for the presence of “cipher voids”; Let’s find out what is important to pay closer attention to: we are only talking about what each user can easily check on their own and understand how reliably they are protected by the VPN service.
Apply - do not use a secure connection via the https - ssl protocol
Text by points:
For those readers who have just wondered about vpn - and this article seems to be something that is not clear, I give the most useful links, by clicking on which you can find out - there, by the way, it discusses in more detail what an SSL connection is... and in general terms below in the text .
I don’t give links to dubious (unscrupulous VPN services), because you yourself, having learned from this article how to check the quality of VPN providers, can easily identify the scoundrels...
secure connection via https - ssl protocol
As sad as it is, I must report that after some tests I carried out, it turned out that several, in general, “not sickly” resources of VPN companies providing advertised services... (don’t be too surprised) still work using the http protocol.
Using an http connection is very good. unsafe(link to article-description just above)! this kind of mess of past technologies makes it possible to easily intercept encryption keys, and, as a sad consequence, to decrypt the Internet traffic of any user of their services.
Today! An important component of the security of the site (and its user) is the indispensable use of the https protocol - “it” uses SSL certificates, which allow you to protect the receipt/transmission of keys... configuration files delivered from the vpn provider to the user.
But for all kinds of protections, there are so-called individual or general encryption keys... More on that below...
individual or shared encryption keys?
Let's call it this - the mistakes - of the VPN providers were like this: many of the services distributed a single key to many servers (and therefore users) - in fact, the user was only protected by the authorization process using a login and password!
Needless to say, in the event of a login and password pair being hacked, the intercepted key (data) allows one to reliably decrypt the client’s (user’s) Internet traffic. Other "Bender" companies simply use different encryption keys for an individual user, but with the same key for all servers. Famously!? ...and you say services/services...)
Only the individuality of the key (for each user) and the server allows for strong protection.
However, the “firms” do not stand still and offer their own branded services!
identified vulnerabilities of “branded” VPN clients
By stipulating the conditions, VPN companies offer their branded VPN clients: no doubt! a branded client is always simpler (in implementing protection) and faster in time, however, it is not always logically safe.
As mentioned, some unscrupulous VPN companies, which still use an unencrypted HTTP connection to the server, recklessly use this negotiation in their branded clients. The whole point of the danger lies in the lack of encryption of the process of receiving/receiving configuration files, etc. - the result is eloquent: keys and configuration files are easily intercepted by third-party scammers and can be used against us - all Internet traffic.
...does “our” client use encryption of data reception/transmission, very easily with the help of various programs - sniffers. They are used by hackers, and as you know - “like with like” - if these programs allow you to intercept traffic, then they will help identify vulnerabilities!.. simply, if you manage to find “configuration secrets” cipher keys, then the service is “rotten” in taste.
Everything is clearly visible in the traffic code that the program provides!
changing the key as security for users
In the process of working on a network (on a computer), with a high degree of probability, various situations arise with the loss of secret keys: either the words of a virus... hacking... or the banal loss of a device - for these reasons, avoiding situations of unintentional “deception” of the user, a decent VPN provider offers the user has options to change keys without any loss of the “authorized” subscription.
Moral: as soon as suspicions creep in regarding personal information security, it is definitely recommended to change the VPN keys.
Maintaining and storing logs of Internet work
Keeping and storing logs will provide an information field for the user (to identify errors) of a particular VPN provider.
This should not be forgotten! since maintaining and remembering/storing logs will allow you to observe the client’s actions on the Internet and his real IP address.
Important!
A VPN representative can thoroughly prove that there is no logging on their (??) server only if he provides full root access (to the client as the administrator of his account, let’s say) for its full verification and control of what is called his own.
how to find out if a VPN is used fingerprint (fingerprint) - in other words, using a VPN
Modern IT technologies make it easy to determine whether a user is using a VPN!? or not...
For the most part, VPN providers do not hide the digital fingerprint of the user. All this is easy to test... //2ip.ru/privacy/
Are encryption algorithms secure?
As it turns out from the article (or rather, by testing), the vast majority (I’m not afraid of this word) of unscrupulous providers use unreliable encryption methods, and this saves the resources of their server. And sometimes, though not often, they do not disdain PPTP, and this has a wide range of vulnerabilities.
You should remember and not forget this circumstance - what technology/encryption algorithms does your VPN provider use?
![]()
If anything is not clear and you still have questions, share them in the comments...
It happens in life that you need 100% anonymity when using the Internet through a browser (I’ll do without examples, otherwise tough guys will come to the comments again and accuse me of incitement and threaten me with department “K”). How to make sure that sites on the Internet (for example Google) cannot identify you and record information about any actions in your file?
It happens that you turn on a VPN with “incognito” mode, you don’t log in anywhere, and AdSense suddenly scares you with painfully familiar ads. How does he determine who is who?
To answer this question, let's conduct an experiment. Let's open tabs in four browsers:
- Tor Browser 6.0.2 (based on Mozilla Firefox 45.2.0);
- Safari 9.0 (incognito mode);
- Google Chrome 52.0.2743.82 (incognito mode);
- Mozilla Firefox 46.0.01 (incognito mode).
And let's see what data they can collect about a person. What do we tell the site about ourselves by typing the URL in the address bar?
We provide unique image rendering options (Canvas Fingerprinting)




Canvas Fingerprinting is a user identification technology developed about 4 years ago at AddThis. The principle of its operation is based on the fact that when, when loading a page, a picture is drawn (rendered) (usually a single-color block in the background color with invisible text), the browser collects a bunch of information about the system for this: what hardware and graphics drivers are available, GPU version , OS settings, font information, anti-aliasing mechanisms and many other little things.
Together, this huge variety of details forms a unique characteristic that can distinguish a user's computer/browser combination from all others in the world. For each, it is written as a string similar to DA85E084. There are matches (according to Panopticlick, the average chance of finding a double is 1 in), but in this case, you can supplement them with other opportunities for identification (more on them below).
Tor asks permission to receive Canvas Fingerprinting, and if you are careful and do not give consent, you can keep this information to yourself. But all other browsers surrender their owner without a single peep.
You can read more about this identification method in Wikipedia.
We break through the database of advertising preferences




Many visited sites are now equipped with scripts for determining Canvas Fingerprint. Having received this unique value, one site can ask another for information about the person. For example, linked accounts, friends, IP addresses used and information about advertising preferences. Use the link below to check which systems have your consumer interests linked to Canvas Fingerprinting.
Tor again asked for the same permission as in the first point and, due to my refusal, nothing was found. Safari found me in 3 databases, Chrome in 13, and Firefox in 4. If you exit incognito mode, then in the latter the number of databases increases to 25, since most of them use good old cookies for identification.
We share the IP address and telecom operator




In Tor, you can change your “host country” using the New Identity button. And “incognito” modes do not hide your IP address (for this you must additionally use a proxy or VPN), but share your approximate location and information about your Internet provider with the site owners.
Revealing your city and the time in it (with geolocation services enabled)




On yandex.ru in Tor, without any location permissions, it showed where I was approximately and what time it was. It's the same with other browsers.
Send us your exact coordinates




Tor didn’t even ask permission to determine the coordinates and simply returned zeros. Safari, Chrome and Firefox asked for the standard resolution (as in normal mode) and did not bother to remind me that I was encrypted and should not reveal such data.
Revealing your city and the time in it (with geolocation services disabled)




Then I turned off location services on the Mac and went back to yandex.ru. Tor made the site think that I was in Romania, but left the time in Moscow (due to the mismatch of IP and time zone, it will be possible to ban VPN providers at once in the event of a ban). In other browsers everything remains the same.


The fact is that Yandex does not need GPS (or WPS data from the device) to determine location. After all, he has a “Locator”! Logged into the network via Wi-Fi? The access point is already in the database (see article). Did you give yourself internet from your phone? The cell tower will be rented.
We provide information about language settings




Another sure sign of a VPN lover is that the language does not match the country whose IP he is using. Tor let me down - its language is always English (but it can be changed, but I thought it should change automatically depending on the country). The rest of the settings are the same as in normal mode.
We tell you everything about your browser and system

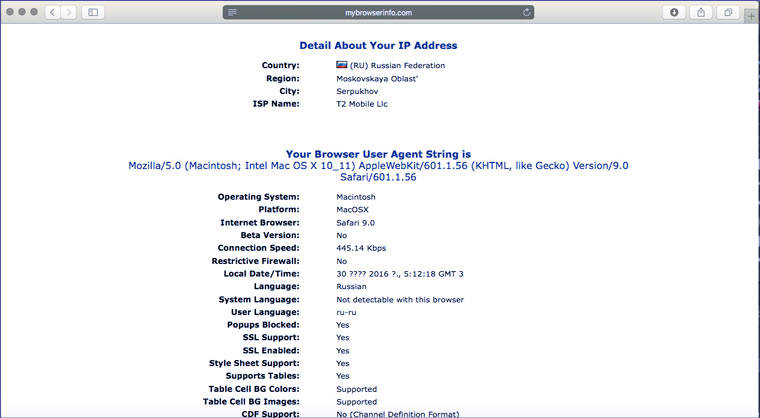

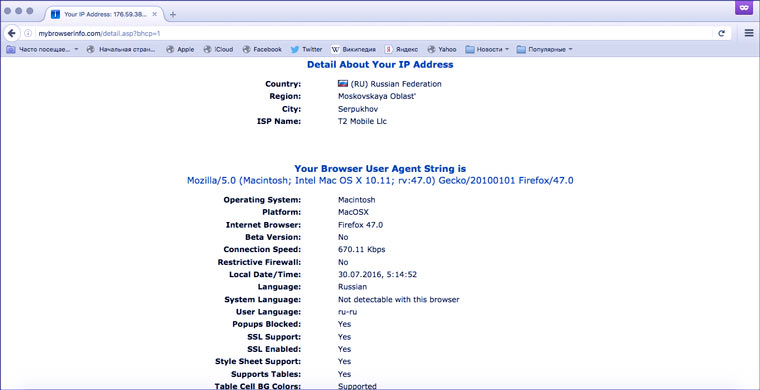
Operating system, connection speed, monitor color characteristics, support for different technologies, browser window width, Flash version - a bunch of little things that complement the unique characteristics of the user. Tor manipulates some of this data (Windows 7 example), but other browsers are completely honest.
A person can change the IP, turn on “incognito”, and the script to raise prices will quickly calculate: “Who is this guy who came to us with a slow Internet, an old version of Flash and Windows XP for the second time, but now decided to pretend to be a resident of the Seychelles? We’re increasing it by 20%!”
We share a list of installed plugins



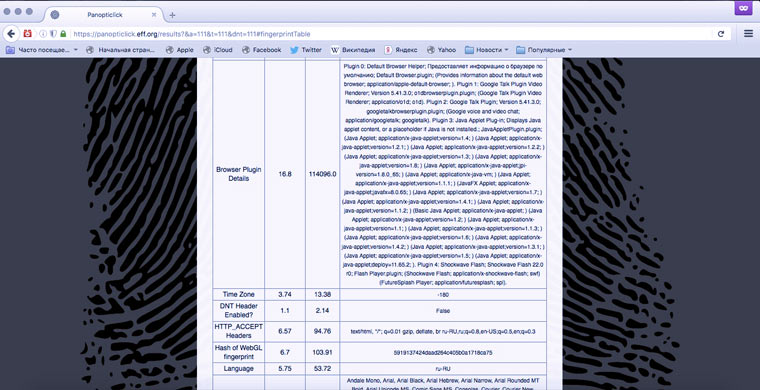
Another characteristic that adds uniqueness to a person is the list of plugins (with version information) installed in his browser. Tor hides them. Other browsers do not.
As you can see, Tor Browser provides good anonymity. But historical facts suggest that if a person does something really serious using the onion network, then he will still be sometimes they find. Everyone probably remembers the revealing story with the founder of Silk Road (a drug store) Ross Ulbricht.
And “incognito” modes are only needed to surf on someone else’s computer and not leave traces. In addition, you can block JavaScript, this will reduce the number of possible identification methods, but many sites will become unusable.
Open the list of fonts installed on the system (=> programs)

In addition to the experiment, I would like to talk about another interesting feature of modern browsers. Any site can get a list of fonts installed on the system. Many applications have their own unique fonts, and by using them you can determine a person’s occupation. And based on this, show him advertisements. In Tor and incognito mode this does not work (or the list is too short).
All this is the tip of the iceberg
To protect against the above identification methods, there are special plugins for different browsers. But you shouldn't waste effort installing them. Since they cannot protect against the collection of all possible information.
After all, in the article I showed the simplest and most understandable examples of how browsers collect information about us. But there could be much more of them: flash cookies, Silverlight cookies, time lag behind the standard time (many have at least 0.2-0.8 seconds) - many little things that would be superfluous. After all, the reader already understands that by opening a browser, he communicates a huge amount of information about himself to the world and demonstrates a set of unique characteristics that distinguishes his computer from all others.
What is the threat of all this information gathering?
You need to collect information about the majority of people on the planet for only one purpose - to increase the click-through rate of advertisements in order to earn more money from it. In principle, this is only beneficial - it is easier to find some goods or services.
More advanced identification methods are useful for stores to collect information about customers. So that a person cannot access the site under a different IP/disabling cookies and remain unrecognized. Language, time, rare font/plugin, monitor characteristics, a typical error in the search query you came from - and that’s it! Take off your skates, we recognize you. There is no doubt, this is the same person who placed order #2389 a year ago. With this data, automated marketing systems can sell him more.
Or, naturally, all this can be used by the intelligence services. But who knows how everything works there.
Previously, we described a rather smart way to leak your real IP address using the protocol. In addition to this method, there are also other methods for determining your real IP address. Today we will tell you about the basic principles of ensuring your security and anonymity on the Internet.
http://witch.valdikss.org.ru/ - allows you to determine what type of connection you are using and whether you are using a VPN.
http://2ip.ru/privacy/ - allows you to collect a lot of additional information about your browser, connection type and IP address.
https://diafygi.github.io/webrtc-ips/ - determines your IP address using the WebRTC protocol.
We have selected a kind of checklist for you that would answer whether you are “scorched” or not? At the moment, the list consists of 12 verification methods, which will be discussed below, including how not to fall for them, but first, the simplest ones in order.
HTTP proxy headers
Some proxies append their headers to the request that the user's browser initiates. Often this is the user's real IP address.
Make sure that the proxy server, if it writes anything in the headers listed below, is at least not your address:
HTTP_VIA, HTTP_X_FORWARDED_FOR, HTTP_FORWARDED_FOR, HTTP_X_FORWARDED, HTTP_FORWARDED, HTTP_CLIENT_IP, HTTP_FORWARDED_FOR_IP, VIA, X_FORWARDED_FOR, FORWARDED_FOR, X_FORWARDED, FORWARDED, CLIENT_IP, FORWARDED_FOR_IP, HTTP_PROXY _CONNECTION
Open HTTP proxy ports
The IP address from which the request to our page came can say a lot. For example, can you see what ports are open on that side?
The most interesting ports are 3128, 1080, 8123. If you do not use them, then you can completely avoid unfounded suspicions about using 3proxy, SOCKS 5 or Polipo.
Open web proxy ports
As with HTTP, a web proxy can be set to any port, but we wanted the test to work very quickly, so we limited ourselves to the reverse connection to ports 80 and 8080.
Is the web page being given away? Great! At the moment we can detect PHProxy, CGIProxy, Cohula and Glype.
Suspicious host name
Having an IP address, you can try to resolve the client’s hostname. Stop words that may hint at a tunnel: vpn, hide, hidden, proxy.
You shouldn't link domain names to your personal VPN, and if you do, you should avoid "speaking" names.
Difference in time zones (browser and IP)
Based on GeoIP data, you can find out the country by the user’s IP, and therefore his time zone. Next, you can calculate the time difference between the browser and the time corresponding to the time zone of the VPN server.
There is a difference? This means the user is probably hiding.
For Russia there is no exact base of latitude and longtitude for regions, and since there are many time zones, in the end result we do not take these addresses into account. With European countries it’s the other way around; they are very good at firing.
When switching to a VPN, you need to remember to change the system time, change the time in the browser, or work with Russian proxies.
IP affiliation with the Tor network
If your IP address is a Tor node from the list check.torproject.org/cgi-bin/TorBulkExitList.py, congratulations, you're burned.
Nothing criminal, but the fact that you are hiding is not very encouraging.
Browser Turbo mode
By collecting the IP address ranges of Google, Yandex and Opera, and comparing them with the user address, we can assume the use of traffic compression services in the browsers of the corresponding companies.
As a rule, such services also leak your real address in the headers. As a means of anonymization, you should not rely on traffic compression.
Web proxy definition (JS method)
By comparing window.location.hostname with the host of the requested page, you can determine whether a web proxy is being used.
Web proxies are not reliable in principle, so it is better to bypass such anonymization methods completely.
IP leak via Flash
Adobe Flash works very well past custom proxies. By initiating a connection to our server, you can find out the user’s IP.
By running a special daemon that logs all incoming connections with tag keys, you can learn a lot. The best way to avoid revealing your address is to not use Adobe Flash at all, or disable it in your browser settings.
Tunnel detection (two-way ping)
By running a ping to the client IP from our server, you can find out the approximate length of the route. The same can be done from the browser side, XMLHTTPRequest pulls an empty page of our nginx. The resulting loop difference of more than 30 ms can be interpreted as a tunnel.
Of course, the routes there and back may differ, or the web server may be a little slow, but overall the accuracy is quite good.
The only way to protect yourself is to deny ICMP traffic to your VPN server.
DNS leak
Finding out which DNS the user uses is not a problem; we wrote our own DNS server, which records all calls to our uniquely generated subdomains.
The next step was to collect statistics on several million users, who uses what DNS. We linked to providers, discarded public DNS and received a list of DNS/ISP pairs.
Now it’s not at all difficult to find out if a user introduces himself as a subscriber of one network, but uses DNS from a completely different one.
The problem is partially solved by using public DNS services, if this can be called a solution.
Leak via VKontakte
This is not a leak of an IP address, but we still believe that by giving away the names of authorized users to everyone left and right, VK is leaking private data that undermines the anonymity of surfing.
More details can be found in the documentation here
